Magento critical security patches SUPEE-6788, SUPEE-6482, SUPEE-6285, SUPEE-5994, SUPEE-5344, SUPEE-3762, SUPEE-1533 (Shoplift)
Shoplift is a dangerous Magento bug. It allows hackers to take e-commerce store under a full control. The threat was discovered by Check Point. You can easily fix it with the help of patch SUPEE-5344. A lot of Magento stores are still vulnerable, because they haven’t applied the patch yet. Below, you we show how to fix the problem.
UPD (15.05.15): SUPEE-5994 Magento security patch
UPD (08.07.15): SUPEE-6285 Magento security patch
UPD (08.07.15): Magento Security Alert Registry
UPD (05.08.15): SUPEE-6482 Magento security patch
UPD (17.09.15): SUPEE-3762 Magento security patch
UPD (09.10.15): Magmi and Nginx
UPD (21.10.15): Guruincsite Magento Issue and SUPEE-6788 Magento security patch
UPD (24.11.15): Magento Security Patch SUPEE-6788 Performance Issues
UPD (28.01.16): SUPEE-7405 and SUPEE-7616
Magento Security Suite by Amasty
Table of contents
- SUPEE-8788
- SUPEE-7405 and SUPEE-7616
- Magento Security Patch SUPEE-6788 Performance Issues
- Guruincsite Magento Issue and SUPEE-6788 Magento security patch
- Magmi and Nginx
- SUPEE-3762 Magento Security Patch: Denial of Service flaw
- SUPEE-6482 Magento Security Patch
- SUPEE-6285 Magento Security Patch
- SUPEE-5994 Magento Security Patch
- Hacked Magento reports / How to check if you Magento store is hacked
- Issues and troubleshooting after patching
- How to check the latest patch version applied to Magento
- How to Install Magento via Composer with all security patches:
SUPEE-8788
We describe SUPEE-8788 Magento security patch here: SUPEE-8788 – A New Magento Security Patch.
SUPEE-7405 and SUPEE-7616
Magento Community Edition 1.9.2.3 has been released and we also got two new patches: SUPEE-7405 and SUPEE-7616. And while the new version of the platform offers an update to the USPS API, the patches improve the security of your Magento website.
As well as in case of some previous updates, there were no confirmed attacks caused by the new vulnerabilities, but they can be exploited to access some sensitive data – the same old song! Thus, we recommend you to install new patches or to update your ecommerce website to Magento Community 1.9.2.3.
SUPEE-7405 (Security Patch Bundle )
Instead of publishing a single security patch, Magento has published a bundle of patches dubbed SUPEE-7405. All of them are aimed at Magento 1.x resolve some security-related problems. For further information, check the official page of the Magento security patch here: .
SUPEE-7616 (USPS Patch)
As for SUPEE-7616, it is designed to prepare your store to revamped USPS conditions which include new services, rates, and package names. So, with the patch, you will get the following changes:
- Retail Ground is now the name of Standard Post
- Flat Rate Box for Priority Mail Express Eliminated
You can download bothe Magento security patches at the same location. You only should:
- Go to the .
- Click the tab called Release Archive.
- Find Magento Community Edition Patches.
- Find the listing for SUPEE-7405.
- Select your current Community Edition version.
- Hit the Download button.
- Follow further instructions.
Magento Security Patch SUPEE-6788 Performance Issues
The Magento Security Patch SUPEE-6788 causes some performance issues. Dima Soroka describes them in his article here: . Furthermore, he offers a performance improvement for the patch: .
Guruincsite Magento Issue and SUPEE-6788 Magento security patch
Guruincsite Magento Issue has been discovered recently. Thousands Magento websites are already vulnerable, so it is extremely important to check if your store is not infected. For further information about the problem, check this article: Guruincsite Magento Disaster.
To prevent your Magento website from the new disease, install a new security patch SUPEE-6788. Please note that the patch may provide an impact on your extensions. ; .
SUPEE-6788 addresses more than 10 security issues, including such important problems as information leak and remote code execution vulnerabilities. Since the patch breaks backward compatibility and could change a way your extensions and customizations work, check the that may impact your Magento website.
The SUPEE-6788 Magento security patch is available for Magento Enterprise Edition 1.7+ and Magento Community Edition 1.4+. It is possible to upgrade your store to Magento Enterprise Edition 1.14.2.2 or Community Edition 1.9.2.2 to implement the patch. If you don’t want to upgrate your website, check the tutorial below.
– This script attempts to find and automatically resolve major problems from the patch. It does this in two stages: analyze, and fix.
How to download and install SUPEE-6788 Magento security patch
SUPEE-6788 requires all previous security patches to be installed. you must first implement all previous security patches. This will ensure that the patch works properly.
If you are a Magento partner, go to the and select the following options: Technical Resources and Download on the Enterprise Edition panel. Then, go to Magento Enterprise Edition/Patches & Support and find the “Security Patches – October 2015” folder: SUPEE-6788 is located there.
If you are an Enterprise Edition merchant, open , go to the Downloads tab / Magento Enterprise Edition / Support Patches and find the “Security Patches – October 2015” folder. Download and install SUPEE-6788.
If you are a Community Edition merchant visit the Community Edition and find the SUPEE-6788 Magento security patch there.
Although SUPEE-6788 has been released, admin routing changes are turned off by default. It means that the patch includes the fix, but that it will be disabled after you install it. As a result, you get additional time for making updates to your code. Note that Magento extensions and customizations should be updated in order to work with SUPEE-6788.
To enable the admin routing capability for extensions after install the patch go to Admin/Advanced/Admin/Security.
Resources necessary to master the SUPEE-6788 Magento security patch update
- &
- / Magento 1.9.2.2 / EE 1.14.2.2
-
- n98-magerun dev:template-var – use it to find non-whitelisted vars/blocks which are compatible with SUPEE-6788 and Magento 1.9.2.2
- n98-magerun.phar dev:old-admin-routing – use this command to find extensions that utilize old-style admin routing incompatible with SUPEE-6788 and Magento 1.9.2.2
- – this tool finds and automatically resolves major problems related to the SUPEE-6788 patch
SUPEE-6788 Magento Security Patch Custom Blocks (and Variables) Issue
After installing the SUPEE-6788 Magento security patch, some custom blocks disappear from the front page, because Magento has added new restrictions in the blockDirective method with the security patch. You can find out if a block type that needs to be displayed is allowed inside a permission_block database table. A new code in Mage_Core_Model_Email_Template_Filter class checks if it exists in the table. In order to resolve the problem with custom blocks, which are not listed in permission_block and consequently will not be displayed, you should:
- define your custom blocks used in the cms {{block}}directive
- under System/Permissions/Blocks add your block type as allowed.
Now, you can open your “app/code/core/Mage/Core/Model/Email/Template/Filter.php” file in a text editor, find “public function blockDirective” somewhere around the 169th line, and add the following line
|
1 |
Mage::log($blockParameters[‘type’], null, ‘blocks_used.log’, true); |
Thus, you will be able to log all blocks that Magento is checking:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
// ... /* Mage_Core_Model_Email_Template_Filter */ public function blockDirective($construction) { $skipParams = array('type', 'id', 'output'); $blockParameters = $this->_getIncludeParameters($construction[2]); $layout = Mage::app()->getLayout(); if (isset($blockParameters['type'])) { Mage::log($blockParameters['type'], null, 'blocks_used.log', true); if ($this->_permissionBlock->isTypeAllowed($blockParameters['type'])) { $type = $blockParameters['type']; $block = $layout->createBlock($type, null, $blockParameters); } } elseif (isset($blockParameters['id'])) { $block = $layout->createBlock('cms/block'); if ($block) { $block->setBlockId($blockParameters['id']); } } // ... |
Now, you only have to surf through all pages on your Magento website while block types will be automatically logged inside the var/log folder. Copy them and add to already allowed block types. The same is about variables, as they can be also affected by the SUPEE-6788 Magento security patch. Variables can be added under System/Permissions/Variables.
Plugins that use custom variables should be updated. Check the following example:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
if (version_compare(Mage::getVersion(), '1.9.2.2', '>=')) { $installer = $this; $connection = $installer->getConnection(); $installer->startSetup(); $installer->getConnection()->insertMultiple( $installer->getTable('admin/permission_block'), array( array('block_name' => 'core/template', 'is_allowed' => 1), array('block_name' => 'catalog/product_new', 'is_allowed' => 1), ) ); $installer->endSetup(); } |
Sources: and
Magmi and Nginx
Magmi and Nginx are two new security vulnerabilities that have been discovered recently. Fortunately, you can easily fix them. Check this blog post – Beware of Nginx and Magmi Data Import Tool – for further information.
SUPEE-3762 Magento Security Patch: Denial of Service flaw
This bug crashes the whole shop when a specific API request is made. The affwcted versions of Magento are 1.9.0.0 and 1.9.0.1. The problem can be healed with :
You are redirected to /index.php/install from frontpage or get the following error:
|
1 2 3 4 5 |
PHP Warning: SoapServer::SoapServer(): I/O warning : failed to load external entity "http://hostname.com/index.php/api/soap/index/?wsdl=1&wsdl%2F_vti_bin%2FListData_svc%2F%24metadata=" in /var/www/html/lib/Zend/Soap/Server.php on line 811 |
quickly fix it by putting the following code on top of index.php (thanks to Ben Lessani):
|
1 |
libxml_disable_entity_loader(false); |
SUPEE-6482 Magento Security Patch
A new Magento security patch called SUPEE-6482 has been released! This time it fixes 4 security issues related to APIs and cross-site scripting. Luckily, there are no victims of these bugs, so the patch is a preventive measure. The issues are described below.
-
Cross-site Scripting with Unvalidated Headers
This problem is possible only on a server with specific configurations. Since an unvalidated host header leaks into a page and an attacker can inject any HTML or JavaScript code adding fake forms for example, all store customers are under risk.
-
Autoloaded File Inclusion in Magento SOAP API
The issue causes code to be autoloaded. This happens because of SOAP API request incorrect validation. Again, the problem requires specific settings, but with appropriate conditions, attackers can load code remotely, as well as log in first with API credentials.
-
XSS in Gift Registry Search
This threat is aimed at registered users. Attackers can thieve cookies and impersonate your customers.
-
SSRF Vulnerability in WSDL File
Due to incorrect encoding of API password, attackers are able to probe internal network resources as well as include remote files.

Support
The SUPEE-6482 Magento security patch was designed for both Magento Community and Magento Enterprise Editions. Being part of Community Edition 1.9.2.1, it is supported by CE 1.4+. For EE, the patch is available since 1.7 version of the platform. It will be embedded into Enterprise Edition 1.14.2.1.
Download
The SUPEE-6482 Magento security patch requires all previous security patches to be installed. Community Edition merchants can download the patch on the Community Edition , or to 1.9.2.1. Enterprise Edition merchants can find the improvement on > Downloads tab, > Magento Enterprise Edition > Support Patches. There is also an ability to upgrade to 1.14.2.1.
SUPEE-6285 Magento Security Patch
The SUPEE-6285 Magento security patch introduces a new level of security. It fixes a weakness that has been recently found in Magento. Luckily, there are no ecommerce shops attacked owing to this issue, but it doesn’t mean you can delay the installation of SUPEE-6285. Deploy the patch immediately and you will provide your store with an additional security level.
First of all the SUPEE-6285 Magento security patch blocks attackers. It prevents them from getting an access to the orders feed. Thus, you preserve personal data. Then, the patch fixes a number of security gaps, such as a cross-site scripting and a request forgery, or vulnerabilities related to the error path disclosure.
The patch is available for Magento Enterprise Edition 1.9+ and Magento Community Edition 1.4.1-1.9.1.1.
Since the SUPEE-6285 Magento security patch is a part of Community Edition 1.9.2, you can easily fix all security problems by upgrading your ecommerce website to the latest version of the platform. The download link is here: Magento Community Edition 1.9.2.
Please note that SUPEE-6285 can be implemented only if SUPEE-5994 has been already installed on your website. To check if everything works as expected, use a development environment first.
The full list of SUPEE-6285 Magento security fixes
- Customer Information Leak via RSS and Privilege Escalation
- Request Forgery in Magento Connect Leads to Code Execution
- Cross-site Scripting in Wishlist
- Cross-site Scripting in Cart
- Store Path Disclosure
- Permissions on Log Files too Broad
- Cross-site Scripting in Admin
- Cross-site Scripting in Orders RSS
Since the SUPEE-6285 file consists of more than 1,100 lines of code, it provides lots of changes. The patch includes 350 additions and 100 removals. Thus, there are several strict requirements as well as possible errors. You can check all of them .
And is a detailed description of SUPEE-6285. If you don’t know how to install the patch, look at .
If you don’t know whether your Magento version requires the SUPEE-6285 Magento security patch or any other previous improvement, check a Magento patch requirement/compatibility spreadsheet by John Knowles. It is available in Google Docs divided into two parts. The first one is related to Magento Enterprise Edition. The second part shows us patch requirements and compatibilities of Community Edition. Both provide information on all available patches, their release dates, compatibility with available versions of the platform, as well as an installation necessity. You can find the spreadsheet .
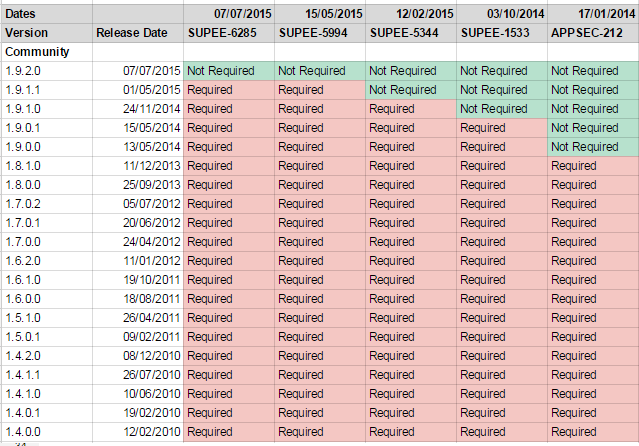
Magento Security Patch List
Magento Security Alert Registry
With Security Alert Registry, Magento introduces a new approach to safety. The new service is designed to inform you about all the latest vulnerabilities. Fill in a form and send your request to get all the latest information related to the Magento security issues.
SUPEE-5994 Magento Security Patch
Magento has released a new patch – SUPEE-5994. It’s aimed to fix the set of security problems and multiple bugs related to the safety of your e-commerce store.
All versions of Magento CE are impacted, that’s why it is extremely necessary to install SUPEE-5994 patch immediately.
The SUPEE-5994 Magento security patch should be installed after SUPEE-5344 – Shoplift patch.
Hit to download SUPEE-5994 security patch. It is available for CE 1.4.1– 1.9.1.1.
We strongly recommend you to start your work with the patch from a development environment. Before deploying it to a production site, don’t forget to make a backup.
___________________________________
Thousands of stores are not updated just because their owners are not informed, they lack of technical support, or their hosting does not provide SSH access. Of course, there are lots of other issues. Being a part of Magento community, we always try to take care of other dwellers of Magento ecosystem, so we share this information with you. We also hope, you will share it with other Magento members.
First of all, we recommend you to use this link – – it’s the source of main information about the problem. You will also find there some stats. The video below demonstrates Magento Remote Code Execution (RCE) Vulnerability
Use the below link to check, if your Magento store is affected:
The good news is that Magento 1.9.1.1 already includes all patches (but not the recent SUPEE-5994 !). You can fix Shoplift by simply upgrading it to the latest version. Below you can find guides and how-tos on the upgrade:
There is also a complete guide on patching other versions of Magento:
Or you can use this one:
Want to apply patches without SSH and use Core Diffs instead? Hit the below link
Another guide based on downloaded patched core files
The appropriate discussion on Magento Stack Exchange. You can find all possible ways of patching there.
Hacked Magento reports / How to check if you Magento store is hacked
Check the below links to see Hacked Magento reports. You will learn how to check whether your store is hacked or not, and what to do, if the store is hacked after applying patches.
Issues and troubleshooting after patching
Some old versions of Magento (probably 1.7.x and 1.8.x) can have issues during applying the patch. We strongly recommend you to make backup of all files affected by patches (you can find them on the below links).
Hunk # FAILED
Hunk # FAILED – in most cases it means that you are using a wrong version of patch which is not suitable for the version of your Magento store, or you have some required server stuff missed. Check the below links to get more help.
However, this issue can also occur with the correct patch on Magento 1.8.x. To solve this problem, you should upload patched files manually (use the above links). And don’t forget to make backups of affected files!
Fatal error: Class Varien_Db_Adapter_Pdo_Mysql
Fatal error: Class Varien_Db_Adapter_Pdo_Mysql contains abstract methods and therefore it must be declared – this issue often happens on old Magento versions (1.7.x) even if you use the correct patch. In that case we suggest to replace lib/Varien/Db/Adapter/Pdo/Mysql.php with a file from patch for more recent Magento version, such as 1.8-1.9 (we have successfuly fixed this error for our several MAgento 1.7 projects). Hit the below link to download the file
You should also check official Magento forum to get more information about the patch and update. Currently, there are a lot of appropriate discussions there:
More information on patch and advices to prevent Magento hacking
Class ‘Mage_Install_Controller_Router_Install’ not found
SUPEE-5994 Patch installation error (fails on lib/PEAR/)
If you have deleted /downloader, you can use a special Magento Security Patch SUPEE-5994 (Magento CE 1.6 – 1.9 / EE 1.11 – 1.14) WITHOUT DOWNLOADER PATCHES
How to check the latest patch version applied to Magento
First of all, you need an FTP access. Then you should check the app/etc/ directory. You can find applied.patches.list file there, which is added when the patch is applied. Being a diff file, the patch shows what it should change when you open it. You should also check in the targeted file if it is changed.
Or you can use a Philwinkle_AppliedPatches Magento module. This tool provides you with the ability to check all applied patches right from the Magento admin. Philwinkle_AppliedPatches utilizes the aforementioned applied.patches.list file to create a list of applied patches. The module doesn’t work, if you do not retain the aforementioned file or commit to source control. If the file is not readable by the web server user, Philwinkle_AppliedPatches also doesn’t work.
How to Install Magento via Composer with all security patches:
If you have any issues or errors while applying Magento core patches, or you have questions related to this topic, let us know in comments – we will try to help!