Magento Security Ultimate Guide

Thousands of Magento websites have been hacked recently. Luckily, there are several useful methods designed to fix the current problems. If your e-commerce website is insecure, then you should hurry up to prevent the undesirable consequences. If your store is affected, it is also important not to delay the solution of the problem. In the post below, we gathered all important information about Magento security issues, which will be useful in both cases.
Magento critical security patches SUPEE-5994, SUPEE-5344, SUPEE-1533 (Shoplift) (all official Magento security patches)
Table of contents
- 1 Impacts of a Hack
- 2 Magento Security Vulnerabilities and Common Hacking Techniques
- 3 Magento Security Tips
- 3.0.1 Name & Password
- 3.0.2 Custom Path for the Admin Panel
- 3.0.3 Two-Factor Authentication
- 3.0.4 Encrypted (HTTPS/SSL) Connection
- 3.0.5 File Upload with Secure FTP
- 3.0.6 Pre-Defined IP Addresses for Administrators
- 3.0.7 Malicious PHP Functions
- 3.0.8 Directory Listing
- 3.0.9 MySQL Injections
- 3.0.10 Other advices
- 4 Restoring E-Commerce Websites After Hacker Attack
- 5 Aspects Important for Every Security Improvement
- 6 Magento Security Extensions
- 6.1 Amasty Security Suite
- 6.2 Nexcess.net Alarmbell Extension for Magento
- 6.3 ET IP Security
- 6.4 SecureTrading
- 6.5 Trusted Shops with Trustbadge
- 6.6 Authorize.Net CIM with Recurring Profiles
- 6.7 Enhanced Admin Security: Two-Factor Authentication
- 6.8 Magento: Two-Factor-Authentication
- 6.9 MageFirewall Security
- 7 How to Evaluate 3rd Party Extensions?
- 8 To Use or Not to Use Magento Connect…
- 9 Magento & Symlinks
- 10 Nginx Webserver Security
- 11 CloudFlare
- 12 Magento Security Alert Registry
- 13 Report Your Security Issues Here
- 14 Sources
UPD (21.10.2015): Guruincsite Magento Issue and The SUPEE-6788 Patch
Since thousands Magento websites are already infected with the Guruincsite malware, so it is extremely important to find out if your store is not infected and prevent it from the disease. For further information, check this article: Guruincsite Magento Disaster.
SUPEE-6788 has been released to help you with solving the Guruincsite problem. For further information about how to download and install the patch to remove the problem, visit our Magento security patches post.
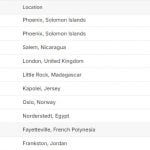
UPD (26.10.15): 80% of Magento shops worldwide are still vulnerable
80% of Magento shops worldwide are still vulnerable. Check the below infographic by Byte for further information. Alternatively, you can read the whole article related to the problem (the infographic is the illustration of the article). It describes the reason why people do not patch their Magento websites, so it might change your opinion related to the security problems.
– a source of security vulnerabilities.
Impacts of a Hack
Let’s start with the importance of this problem. Chances are, that your Magento website has no visual changes – everything looks and works as before. Thus, you might think that the problem is exaggerated. But don’t be deluded by this superficial impression. The issue is much more dangerous as it might seem at first glance.
Say “Hello” to unauthorized credit card transactions! Hacked e-commerce website is absolutely insecure place for your customers. A malicious code will never provide any visual changes to the store, so you will know about the threat only after your customers begin to complain. Or you can ask specialists to scan your Magento website periodically.
Malicious code is able to steal payment details. Hackers add extra lines into a function and start to receive information submitted by your customers during the checkout. Most Magento sites provide a checkout form with a field for customers’ credit card details. The system encrypts this data and sends it to a payment gateway, but there is a short period of time, when credit card details ARE NOT ENCRYPTED. If your store is hacked, malefactors can easily steal the unencrypted information.
Besides Magento, all other e-commerce tools, which require credit card details directly on a site, can be hacked. Solutions, which redirect customers to a payment gateway website, are much more safe.

Stolen Credit Card Details
Unfortunately, this is only a half of the problem. As a store owner, your are also under a threat. There are cases, when hackers set their PayPal accounts instead website owner’s account. Thus, all the income goes to malefactors.
For online customers we recommend to use websites, that send to a payment organization site to complete the purchase. If the desired goods are only on the website, that doesn’t sent to outer platforms, then you should check if it is secure. Use a free tool, check , or try to surf for some reports on the web. Additionally, you can use more secure credit cards. For example, Visa 3-D Secure provides additional levels of authentication.
As an e-commerce website owner, you can outsource payments to PayPal, Google Wallet, Stripe, and other third-party payment solutions. If your e-commerce store security is affected, get help quickly. If everything is ok, you should follow these rules:
-
For every element of your e-commerce website, you should create unique and strong passwords.
-
Implement the integrity control for the database and files.
-
Try not to host your online store on the same account with other websites.
-
Protect your e-commerce website with a firewall.
-
Always monitor your site for e-commerce security issues
Below you will find more detailed advices, but first we will describe core Magento security vulnerabilities and hacking techniques.
Magento Security Vulnerabilities and Common Hacking Techniques
Magento security vulnerabilities are almost the same with vulnerabilities of other e-commerce platforms because of similar approach to the development. Often, the problem is in developers which are bounded by tight deadlines. As a result, they just don’t have enough time for creating proper Magento security features, because design and functionality are more important. Thus, security issues are pushed aside. Another reason is in too complex applications, necessary for the implementation of top-notch user experience. Such apps have lots of vulnerabilities, but modern e-commerce is impossible without them (nobody wants to see the downgraded interfaces and features).
Hacking Techniques
SQL injection. With the help of this attack technique, hackers use application vulnerability to get the access to restricted areas. As a result, they are able to steal data or change the functionality of Magento website. This technique utilizes inserting of malicious SQL statements in user’s input.
DDoS. Distributed Denial of Services attack is used in order to make website unavailable to customers. Multiple requests exploit server capacity bottlenecks, and website or some of its functions become non-working.
Broken Authentication / Session Management Attacks. With the help of this technique, hackers get access to accounts by exploiting weaknesses within the authentication process and exploring cookies or sessions IDs.
Cross-site Scripting. This hacking technique is about injecting client-side script into site pages visible to other users. A cross-site scripting is used in order to bypass access controls.
Remote Command Execution. Hackers utilize this technique when an input validation provides them with privileges of the web server while executing OS commands.
Magento Security Tips
Despite Magento is the safest e-commerce platform, there are still some additional security tricks, which make it even more secure.
Name & Password
As mentioned before, you should make all your Magento passwords unique and strong. The same is about admin name. This easy step will help you improve your e-commerce website security. Create a password, that is longer than eight characters. Note, that it should combine numbers, letters, and special characters. Don’t use usernames such as ‘admin’ or ‘administrator’. If your password and username are weak, you can always change them in System > My Account.
Custom Path for the Admin Panel
The default path to the admin panel looks like this: http://storename.com/admin. Everyone knows it, that’s why such path is among Magento security vulnerabilities. By changing it to something like http://storename.com/superadmin , you push your ecommerce website security to a new level. This small step is the best defense against Broken Authentication / Session Management Attacks.
You can always change the Magento admin path in “app/etc/local.xml” file. Find the line which contains “<![CDATA[admin]]>”, and create a new string instead of admin, for example “superadmin” like in the example. The new code should look like this: “<![CDATA[superadmin]]>” .
Two-Factor Authentication
Another important security technique is a two-factor authentication. It adds another security layer to the existing one. The system requires two separate authentications to provide user with the access. Thus, your Magento website becomes two times more secure. You can provide two-factor authentication for your administrators with the help of one of these .
Encrypted (HTTPS/SSL) Connection
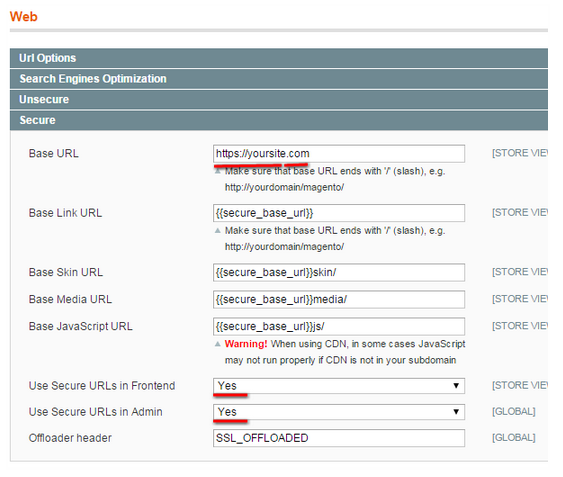
Use of HTTPS/SSL secure URLs is another important technique, which will make your Magento website more secure. Being HTTPS/SSL encrypted, your e-commerce Magento store will also be PCI-compliant. It means that you will get a secure transfer of data between your site and your server. Otherwise, there is a risk that data (database information and login details) will be intercepted by hackers.
To enable HTTPS/SSL secure URLs, you should go to System > Configuration > General > Web. Then, it is necessary to change ‘http‘ to ‘https‘ in Base URL, and enable Use secure URLs for both Frontend and Admin.
File Upload with Secure FTP
In addition to HTTPS/SSL secure URLs, you can also take care of FTP connection with your server. Use SFTP as it provides additional encryption of user credentials. This protocol uses a private key file for authentication. Make sure that file permissions are not set to 777. Otherwise, anyone will be able to write them.
Pre-Defined IP Addresses for Administrators
Magento provides a possibility to set predefined IP addresses for the access to the admin panel, which is another security layer for your e-commerce website. You just have to create a list of these IP addresses. Users with other IP address won’t be able to get the access to the admin panel of your Magento store.
To implement this security feature, find your .htaccess file and enter the following code in it:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
AuthName "Protected Area" AuthType Basic <Limit GET POST> order deny,allow deny from all allow from 172.161.132.13 allow from 153.119 </Limit> |
Thus, you will provide the ability to access your admin panel for user with ‘172.161.132.13’ IP address, and for everyone with IP addresses starting with ‘153.119’. This technique supports the unlimited number of IP addresses.
Then, you should go to Magento root directory and create a new folder called ‘admin’. Copy index.php file of your Magento and paste it here. Now you have to change the relative paths to config.php and Mage.php files. Change the below lines:
|
1 2 3 |
$compilerConfig = '../includes/config.php'; $mageFilename = '../app/Mage.php'; |
You should only add ‘../‘ in these file paths.
Now go to .htaccess file and enter the following lines:
|
1 2 3 |
Redirect permanent /index.php/{admin_path} /admin/index.php/{admin_path} Redirect 301 /index.php/{admin_path} /admin/index.php/{admin_path} |
You will direct users coming to our admin paths to the new directory. ‘{admin_path}‘ indicates the new admin path, manually changed before.
This security step works only with static IP addresses. If your ISP assigns dynamic IP addresses, you shouldn’t implement this technique.
Malicious PHP Functions
There are malicious PHP functions that should be disabled. You can use more secure alternatives instead. To disable these PHP functions, find your php.ini file, open it, and enter the following code:
|
1 |
disable_functions = “apache_child_terminate, apache_setenv, define_syslog_variables, escapeshellarg, escapeshellcmd, eval, exec, fp, fput, ftp_connect, ftp_exec, ftp_get, ftp_login, ftp_nb_fput, ftp_put, ftp_raw, ftp_rawlist, highlight_file, ini_alter, ini_get_all, ini_restore, inject_code, mysql_pconnect, openlog, passthru, php_uname, phpAds_remoteInfo, phpAds_XmlRpc, phpAds_xmlrpcDecode, phpAds_xmlrpcEncode, popen, posix_getpwuid, posix_kill, posix_mkfifo, posix_setpgid, posix_setsid, posix_setuid, posix_setuid, posix_uname, proc_close, proc_get_status, proc_nice, proc_open, proc_terminate, shell_exec, syslog, system, xmlrpc_entity_decode” |
You can add this code to other disable functions from your php.ini file. You can also omit important functions from the above code.
Directory Listing
Directory listing is among other server loopholes. It provides everyone with the ability to see the directory structure and location of all files by simply entering your website’s URL. Thus, you should disable directory indexing. Just add the below code in .htaccess file:
|
1 |
Options -Indexes |
MySQL Injections
In the beginning of this post, we’ve provided an example of MySQL injection. Every Magento website has lots of form fields for user data. Hackers can easily steal this data by injecting MySQL statements. To protect your store from such violation, you should use web firewalls (there are a few apps below).
Other advices
-
Update your Magento to the latest version, as it always provides lots of improvements, bug fixes, and new features including security features. At the same time, there is a possibility of new undiscovered problems related to the latest update.
-
Create backups of your Magento store regularly. It will help you decrease damage of every hack, and you will be able to restore your Magento website faster.
-
Fix all e-mail loopholes. Your e-mail should not be widely known. It also should be protected with unique and secure password.
-
And don’t forget to check the security of your Magento website regularly. This will help you find all issues at early stages.
-
Always update your antivirus software. Chances are, that its older versions will not be able to save your store from latest threats.
-
Know where your browser comes from, as it stores lots of important information about your Magento websites, and try not to save passwords in it. With the access to your computer, hackers will easily get the credentials.
-
local.xml file contains such sensitive data as database credentials and encryption key. Hide it from the public. You can do it by changing the file permissions for local.xml to 600(-rw) or blocking the web access to the entire app directory.
-
Upgrade your OS to the most recent version. It should provides new security improvements.
-
Don’t forget to install Magento security patches. They are developed to fix all current security problems of your Magento store. For example, one of the recent patches is SUPEE-5344.
-
Your hosting provider should be reliable and secure. Note, that some hosting providers are not prepared for hacker attacks.
-
Provide limited permissions on files and documents. For downloadable documents set only read permissions, thus no program will be able to modify them.
-
Disable Magento Connect Manager after installing extensions in order to prevent any random changes.
-
Use only trusted Magento extensions from reliable sources, such as Magento Connect (or not? more info below).
-
Change passwords for outside developers. You can set your ordinary passwords back when the work is done.
-
Check web server logs for errors or suspicious activity. You will be able to detect threats at early stages.
-
Block unwanted countries if you are not shipping worldwide. You can utilize the GeoIP Legacy Apache Module.
-
Check for more tips.
Restoring E-Commerce Websites After Hacker Attack
-
Get the backup of your e-commerce store.
-
Try to find the vulnerability.
-
Change passwords.
-
Try to fix the problem.
-
Don’t forget to put your site offline for a while.
-
Customize the 503 error page in order to ask customers to contact you via other channels.
Aspects Important for Every Security Improvement
You should take the below aspects into consideration before improving the security of every Magento store. They are divided into three categories: Magento security; System security; General questions about the organisation.
Magento Security
-
Where is HTTPS used: over the shop, or only for checkout?
-
Does the site has a custom path to admin?
-
Is the access to this path restricted?
-
How many administrators does the site have? Are any unneeded users active?
-
What about account protection and password encryption for both customers and admins? Are these features standard or customized? Is 2-factor authentication enabled?
-
What Magento version is used?
-
What Magento Security Patches are applied?
-
Is there any custom root level folders or scripts which require remote access?
-
Is an access to test / staging system restricted?
-
What web-services and import/export functionalities are used?
-
How important are those web-services? What are their roles? Are there any unneeded active roles?
-
What are installed extensions?
-
Are they updated?
-
What about PCI-DSS, trusted shops, any other labels?
-
What is the lifetime of Session/Cookie?
-
What third-party software is utilized besides Magento? (e.g. WordPress)
-
What data (both customer and order data) is stored?
System Security
-
What is the PHP version: a recent or an old one?
-
How do file permissions work: running as root or www-data/apache user?
-
Is a proper file permissions set used?
-
What mechanism is implemented: shop specific database-credentials or database is running as a root?
-
What about SSH/SFTP access? Is there a key-based authentication?
-
Is there any service-level agreement with hosting provider about regular updates of OS, PHP, modules, and security features?
Organisation
-
Who is responsible for system updates? Is there someone responsible for security updates?
-
Who has an access to the live-server and live-shop?
-
Where is the code hosted? Who has access to the bare repo? Who has push access?
-
What about the current software development process? How does it look like?
-
Are there automatic checks and code reviews done before deploying new code to staging/test/live?
-
What about regular security audit?
-
What about backups? Is there a regular one? Is it external?
-
What are business continuity and recovery plans?
Magento Security Extensions
Amasty Security Suite is an all-in-one tool that will help you control such aspect of your ecommerce website as actions of administrators, role permissions, backups, and logins. Let’s pay close attention to each feature after the break.
The Alarmbell Magento extension provides notifications each time an admin user is created, edited, or deleted. The module logs data to the standard system.log as well as collects IP and account information of users making the changes. Besides, it can be configured to send notifications for admin account logins. Since attackers gain access to a Magento store by creating an admin user, Alarmbell will help you prevent attacks.
ET IP Security
This admin security extension restricts access to your Magento website by IP address or IP masks, so you don’t have to implement this security technique manually. The module redirects customers, which don’t have access, to the page specified in settings (it can be just a blank page). The module is free.
ET IP Security
SecureTrading
With this Magento module, you will be able to integrate your e-commerce website with STPP – The SecureTrading Payment Pages. This gateway provides secure acceptance of online payments. Your store doesn’t even have to be PCI-compliant (but it should), since all customers are redirected to the servers of SecureTrading for entering card details. This solution relies on iframes and custom CSS / JavaScript. It provides two payment methods: Payment Pages, which is based on redirection to Secure Trading, where credit card details are captured; and API – all information is captured on your server (less secure). This module is also free.
SecureTrading
Trusted Shops with Trustbadge
With the help of this extension, you will provide your customers with information about reliability of your store. The extension shows the Trustbadge, which displays such information as reviews, trustmark, and money-back guarantee in one place. The extension doesn’t provide any security fixes, but it shows that your Magento store is secure. You can download this module for free.
Trusted Shops with Trustbadge
Authorize.Net CIM with Recurring Profiles
Authorize.Net CIM is designed for improved payment secutity of your Magento store. It supports all Magento payment actions, and allows customers to save payment information for future use. As a result, they can enjoy the rapid checkout without disregarding PCI compliance. Authorize.Net CIM supports ACH and recurring profiles. The extension costs $599.
Authorize.Net CIM with Recurring Profiles
Enhanced Admin Security: Two-Factor Authentication
With this Magento module, you will be able to enhance the security of your store by utilizing two-factor authentication. Thus, your admins will have to enter username, password, and security code to log in. The code is generated by the application on a smartphone. It can be used only once within 30 seconds. You can download Enhanced Admin Security Magento extension for $69.
Enhanced Admin Security: Two-Factor Authentication
Magento: Two-Factor-Authentication
This is a free alternative to the previous solution. Backend users with the access to protected resources, are asked to enter one-time security code after the standard authentication. The code is generated by Google Authenticator application.
Magento: Two-Factor-Authentication
MageFirewall Security
Creates the additional layer of security around your Magento website with the help of Magento Firewall. This extension relies on Ninja Firewall rules to block the attackers, blacklist them, and prevent their access to the site. MageFirewall uses scanner to alert you if hackers break into your e-commerce store. In addition, it provides recommendations around your store setup. The extension is free.
MageFirewall Security
How to Evaluate 3rd Party Extensions?
There are 3 different approaches to the evaluation of 3rd party extensions.
Basics approach:
-
Does the extension support the latest Magento version? (If it doesn’t, you will have to spend precious development time on it)
-
Is there official support? If developers actively support their products – it’s a good sign. Such extensions are healthy.
-
What are reviews on this module? Other Magento users can tell a lot about certain extension in reviews.
-
What about refund? If the company provides this option, the module should also be healthy.
Intermediate approach:
-
Class Overrides. Note, that a good module shouldn’t override core classes. It should use Observers instead.
-
Layout Changes. If the module changes layout settings, you should understand, how to fix the problem.
-
Template Changes. How does the module change the current template? Are this changes crucial?
-
Dependencies. If the module depends on other extensions, you should prepare your Magento website for its installation by installing missing components.
Advanced approach:
-
SQL Upgrade scripts. How does the module impacts the DB? If it updates a core table, that’s not good. And it should store the information in a sensible way.
-
Events. Does the module dispatch or observe events? What are this events? What is the influence on other modules?
-
Code Review. What are the coding techniques utilized by this module? Are they acceptable?
-
Potential Issues. Are there any potential issues caused by this module?
To Use or Not to Use Magento Connect…
There are a lot of discussions around Magento Connect. Many store owners still use it, but what are the drawbacks? Is it secure to use Magento Connect? What do you get and what do you lose by utilizing this platform? Hit to find out answers to these and other questions.
Magento & Symlinks
If you hesitate to use Symlinks, you should read . If you already use them, you should also check it. Magento Stackexchange provides a lot of useful information related to Symlinks. All possible reisks and security issues are covered by different developers. Symlinks aren’t necessarily bad, but…
Nginx Webserver Security
Want to identify and block bad Magento traffic? You can easily protect your store with the help of the below guide:
The author provides a list of common attacks and explains how to identify them.
Check the below links to understand what to do with Nginx webserver to make it more secure:
-
Nginx Firewall:
- ()
CloudFlare
CloudFlare provides a new type of security services. Modern digital space is full of various threats ranging from excessive bot crawling to SQL injections and DOS attacks. With CloudFlare, you will get a robust protection against all of these threats. It automatically detects new attacks and blocks them for both the certain website and the entire community.
Magento Security Alert Registry
With Security Alert Registry, Magento introduces a new approach to safety. The new service is designed to inform you about all latest vulnerabilities. Fill in the form and send your request to get all the latest information related to the Magento security issues.
Report Your Security Issues
Sources
- &