Magento 2 SameSite Cookie Guide

Are you ready for the fourth of February? If you don’t know what this date means, you’ve come to the right place. If you know but still look for help, you will find it below. In this article, we explore a new Chrome update and its impact on the entire Internet, e-commerce, and Magento. In an attempt to make the most popular browser faster and more secure and customer experience more private, Google changes the default way of how cookies are treated.
The new improvement is already dubbed the SameSite update. It affects everyone, from website owners to visitors. The update forces you, as a Magento merchant, to explicitly label third-party cookies. If you do not do that, cookies won’t work correctly in the Chrome browser. And as we all know, it is the most popular application people use to interact with the Internet. However, it doesn’t mean that users, who rely on other browsers, won’t be affected. Google sets a new trend so that other companies will join it soon. Let’s explore the update itself and then proceed to our tiny Magento 2 SameSite cookie guide.
Table of contents
- 1 The SameSite cookie updated and the changes it offers
- 2 Reasons behind the SameSite cookie updated
- 3 How to get ready for the SameSite cookie update
- 4 The risks behind the SameSite cookie update
- 5 Magento 2 and the SameSite cookie update
- 6 Cross-Site and Same-Site Cookies Explained
- 7 What’s next?
- 8 Final Words
On the fourth of February, Chrome will be updated to version 80. Although joking about level 80 is fun, it won’t help anyone to deal with the new challenges the new browser version provides. From that day, cookies that do not include particular labels will be inaccessible by third parties. It means that ad tech and analytics companies won’t be able to work with cookies with the “SameSite=None” and “Secure” labels in Chrome version 80 and beyond as they got used to.
Since the current SameSite default for Chrome is “None,” third-party cookies can track users across sites. The update changes the default label to “SameSite=Lax.” It means that cookies are set only when the domain in the URL of the browser matches the domain of the cookie. In this situation, we deal with first-party cookies.
As for cookies with the “SameSite=None” label, they must have a secure flag. It’s a guarantee that they are created and sent only through requests made over HTTPS.
Also, note that with the new update, you can use the “SameSite=Strict” label to restrict cross-site sharing altogether. It is even possible in the case of different domains that are owned by the same publisher.
There are two reasons why Google decided to implement the new approach to cookies. First of all, it is security. Third-party cookies are often utilized in malicious tracking, data leakage, and cross-site request forgery attacks.
You click a link, and a malefactor receives access to your login credentials. Unfortunately, everything is that simple nowadays, but the update is going to change everything. Google always tries to move the web ecosystem to a more healthy dimension; this time, the company is going to succeed as well. Unfortunately, the SameSite cookie update will not affect everyone equally. So, how to get ready?
Although every website is unique in how it relies on third-party cookies, the only general recommendation is related to testing. As a publisher, e-commerce store owner, or anyone else behind a website, you should immediately find out whether your site is affected or not:
- Go to Chrome://flags;
- Enable #same-site-by-default-cookies;
- Enable #cookies-without-same-site-must-be-secure;
- Check whether anything breaks;
- Migrate to HTTPS secure pages, if you haven’t done that yet.
Inspect your website in a test environment!
Also, be attentive to alerts in your developer tools. Thus, you won’t miss how ad tech companies, analytics providers, and other vendors are setting third-party cookies on their sites.
One of the most significant dangers behind the update is that it sacrifices usability. Third-party cookies often participate in logins and remembering user preferences. It happens when a vendor owns a number of different websites and domains. In this situation, a user can log in to an account on one site and stays logged on the others. As a publisher looking to maintain single sign-ons for multiple domains, you need to ensure that your cookie configuration is compatible with the new standards.
If you are a vendor with cookie-reliant audience databases, you may face even more essential difficulties. Since the new standard cookies are not compatible with the old ones, your existing marketing pool may become useless.
Since the SameSite cookie update tends to provide users with more nuanced control of their privacy settings, they may get the ability to remove ad-tracking cookies but prevent on-site login details and preferences from any impact.
As a Magento website owner, you may experience some wide-reaching consequences. Your e-commerce store may utilize cookies that fall into this category. It usually happens when you use secure payment gateways or third-party software solutions, like NewRelic. For instance, you have a PayPal payment gateway on your Magento 2 website. It incorporates an iFrame to enable top-level security. Since the technology is based on third-party cookies, it may not work correctly after the SameSite update is implemented.
Furthermore, you don’t have to use third-party solutions to be affected. Above, we’ve mentioned publishers that rely on multiple domains, sharing cookies for numerous sites. As a Magento 2 store owner, you may also implement this approach to your business, running several e-commerce websites. Thus, the SameSite cookie update will impact the user experience of your customers, changing the functionality of your stores. Not only shoppers but also store administrators are affected. Follow this to see how the community proposes to address it in future Magento releases.
Recommendations for Magento 2 users
As a Magento store owner, you should test the impact of the SameSite cookie update on your website:
- Ask your technical specialists to explore how a development copy of your storefront behaves with the SameSite flag set to Lax or Strict. Thus, you will find out what issues the restricted access to third-party cookies causes and what cookie loading errors occur.
- Conduct User Acceptance Testing. It will let you confirm that you’re not experiencing any issues directly.
- Check notifications from vendors, since they will inform you about any possible problems directly.
Also, pay attention to the following nuances:
- Unfortunately, some languages and libraries do not support the None value yet. As a result, developers should set the cookie header directly. Check this , to discover how to implement SameSite=None; Secure in different environments.
- Also, check a list of to discover browsers that might handle the None value in unintended ways. You will have to code exceptions for them.
- If single sign-on or internal applications are not ready for the update, you may need to implement temporarily reverting Chrome Browser to legacy behavior.
- The same cookies may be accessed in both a first- and third-party context. You need to use separate cookies to get the security benefits related to SameSite=Lax.
Follow this link for further information and the explanation of the situations described above: .
As for same-site cookies, no actions are required. After the new update, Chrome will automatically prevent them from being accessed by external entities. It means that you will leverage the security benefits if no values are set or the SameSite attribute is missing. At the same time, you should consider that applying an appropriate SameSite value (Lax or Strict) is strongly recommended.
As for the readiness of vendors and service providers, monitor Developer Tools console warnings in Chrome 77+. You will see the following notification when a cross-site cookies miss the required settings:

And don’t forget to reach out to your partners to confirm their readiness and discuss enhancements necessary for your Magento 2 website. Thus, you will face the SameSite cookie update fully armed.
Cross-Site and Same-Site Cookies Explained
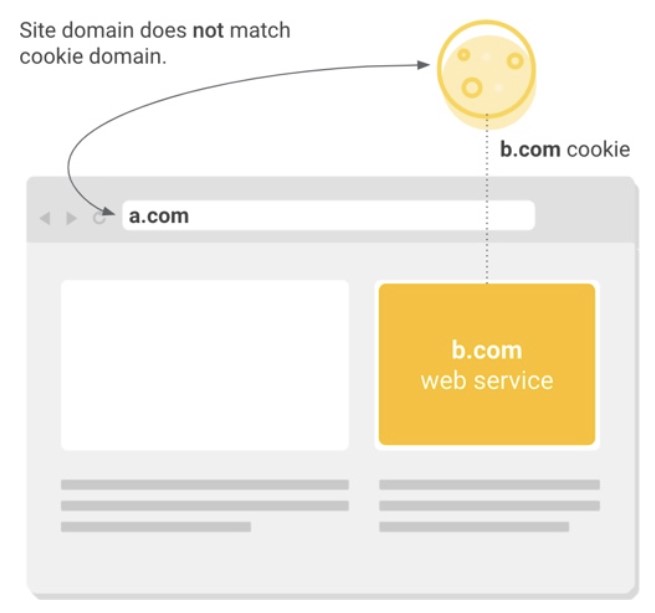
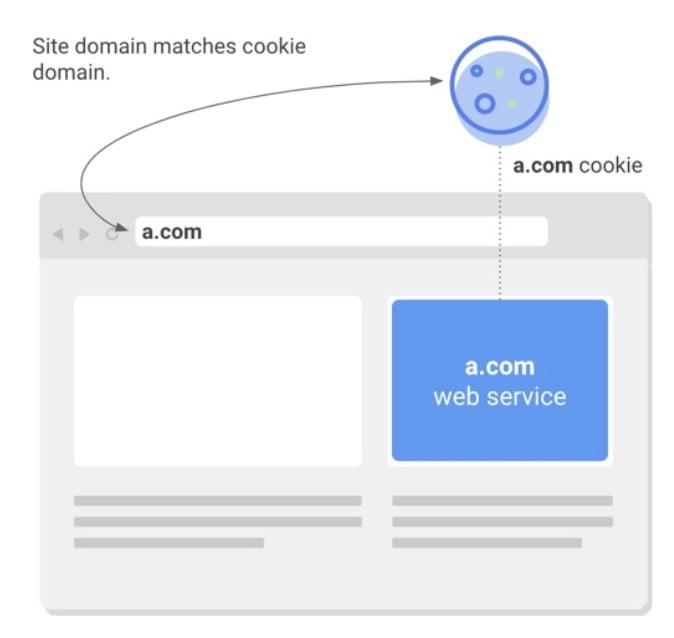
Now, let’s explore several technical aspects of cookies to shed light on the nature of the update. Most websites integrate external services for various purposes and Magento 2 is not an exception. E-commerce stores rely on numerous third-party solutions to provide a top-notch user experience. As a customer, you browse the web while these services store cookies in your browser to access them further. Their primary goal is to deliver more personalized experiences. Of course, cookies are often utilized to measure audience engagement, which, in fact, also positively impacts user experience. But let’s return to our mutton. Every cookie, no matter it is cross-site or same-site, has a domain associated with it. If the associated domain matches a website that is currently opened in a browser, this is considered a same-site context. When it matches an external service, this is regarded as a cross-site context. (First-party and third-party cookies correspondingly.)
It is also necessary to describe a less obvious cross-site use cases, one of which we’ve already mentioned. When an entity owns multiple websites and uses a cookie across them, such a cookie may be considered the third party even though the same entity owns the cookie and the websites. As you might have guessed, the primary condition for a cookie to be a cross-site one is the domain that matches or does not match the site from which it is accessed.
As for same-site cookies, they are considered such, when a cookie’s domain matches the website domain from which it is accessed. This technology keeps people logged into individual websites and remembers their preferences, making the user experience more personalized and flawless.
A new dimension of security and transparency
Today, for first-party cookies, a developer has the option to apply ether SameSite=Lax or SameSite=Strict, preventing external access. However, this practice is not mandatory, so very few developers follow the recommendation. As a result, a large number of same-site cookies are left exposed to various threats, including Cross-Site Request Forgery attacks.
To enter a new dimension of safety and transparency, the new model is secure by default. It means that all cookies are automatically protected from external access unless otherwise is specified. Now, it is necessary to use the following cookie settings:
- SameSite=None that designates cookies for cross-site access;
- Secure that enables access to cookies only over HTTPS connections.
Note that these two measures do not mitigate all risks associated with cross-site access. However, they provide reliable protection against various network attacks.
In addition to security benefits, the SameSite cookie update also enables greater transparency. Thus, users gain control over cookies that are only accessed by a single site. At the same time, they can manage cookies accessed across multiple locations separately.
What’s next?
Google sets a new trend with the SameSite cookie update. Mozilla has already affirmed their support of the new classification model. Microsoft recently announced similar plans but in the form of an experiment. It seems that it is just the beginning because Google plans to replace third-party cookies with browser-based tools achieving an even higher level of personalization and privacy. Support for third-party cookies in Chrome is going to be phased out within the next two years. They will be replaced with browser-based mechanisms. This transition is as part of the ““ initiative. The other plans include:
- Perfect personalization and privacy ratio. Google is going to implement a secure environment for personalization. The company’s goal is to show relevant ads but minimize user data sharing with websites and advertisers. However, it won’t be large scale cookie blocking in the short term, since it negatively affects personalization and reduces the efficiency of ads. As for the long term, we should see utterly new technology as a replacement for cookies.
- In-browser audience targeting. Some processes will be held right in the browser environment to make data more secure and private. Google is going to leverage some privacy-preserving APIs. The company is already exploring how to provide large groups of similar people with ads without letting data leave the browser. It seems that we will soon witness interest-based targeting at a large-group scale with no individual information revealed.
- Conversion measurement should have the same destiny. Being tracked inside Chrome, it will be provided to advertisers through an API. No individual user should be identified in this process.
Final Words
Let’s summarize what we know about the SameSite update and Magento. The most significant change is that Chrome 80 treats all cookies with no declared SameSite value in the same way: they are considered SameSite=Lax cookies. You have to use SameSite=None; Secure parameters to make cookies available for external access. Besides, they should be accessed from secure connections.
And it is not only Google who wants to implement this approach. Other significant browsers are also going to participate in the game. So, if most of your customers don’t use Chrome, it doesn’t mean that you shouldn’t be prepared for the SameSite cookie update. Test your Magento 2 website and check what your partners and vendors of external software solutions say about the impact of the new improvement. Thus, you have a chance to transit to the new rules with no headaches.
You must admit that Google’s SameSite move is a significant change and challenge not only for Magento 2 and e-commerce but the entire web. It is a new trend that will soon be adopted by Firefox and Safari. The update looks like an attempt to find a compromise between the security of personal information and the personalized and efficient operation of the advertising ecosystem.
Of course, this move also reminds us of Google’s monopoly in the sphere of digital advertising. The company changes the entire algorithm the whole industry is based upon. However, it is a significant player who understands the mechanism behind the SameSite move and can leverage it for its purposes much faster than the other players, who still have to spend a plethora of resources, exploring how to get ready for the new conditions.
The world of digital advertising will never be the same again. However, it is not the apocalypse. It is just a new unexplored dimension that tends to make the digital experience of every individual more safe and private. As for Magento 2 vendors, publishers, digital advertising agencies, they have to test their websites and services, following the new requirements, as it is the only way to find out how to leverage the industry change most efficiently.







