Key Security Issues Of The Web 2016
Today, we are going to explore such an important topic as web security. Since there are a plethora of problems related to the IT sector, it is impossible to cover all network security issues in a single article, so we are going to shed light on key aspects only. The following post contains some facts about the most common security threats of the Web. Please note that major security issues in ecommerce are often similar to other segments of the Internet, so this guide is aimed at online retailers, bloggers, and all other kinds of web users.
Table of contents
- 1 Web Security Issues 2016: Insecure Cookies
- 2 Web Security Issues 2016: PHP Version Disclosure
- 3 Web Security Issues 2016: Nginx Version Disclosure
- 4 Web Security Issues 2016: Cross-Site Request Forgery
- 5 Web Security Issues 2016: Missing X-Frame-Options Header
- 6 Web Security Issues 2016: Forbidden Resources
- 7 Web Security Issues 2016: Email Address Disclosure
- 8 Web Security Issues 2016: Robots.txt With Potentially Sensitive Content
- 9 Web Security Issues 2016: Outdated Software
- 10 Web Security Issues 2016: Full Path Disclosure
- 11 Web Security Issues 2016: Unexpected Redirect Response Body
Web Security Issues 2016: Insecure Cookies
Insecure cookie is one of the most common security issues of the Web. If a cookie is transmitted over HTTPS but is not marked as secure, it could be stolen by a malefactor. Consequently, your traffic will be intercepted and decrypted, and the attacker will hijack a victim’s session. In order to prevent your website from this software security issue, you should mark all cookies used within the app as secure. To make your cookies totally secure, utilize the following tips:
- Send a cookie to your app only.
- Don’t share it with subdomains.
- Use a secure connection.
- Protect against XSS exploits.

For further information about configuring the cookie, follow this links: and .
Web Security Issues 2016: PHP Version Disclosure
A PHP version disclosure in a target web server’s HTTP response is another common software security issue. It helps attackers get a deeper insight into your systems. As a result, the malefactors can generate better planned attacks targeted at the specific PHP version.
The disclosed information is often used for harvesting data on security vulnerabilities of the identified PHP version. In order to protect your website from this information security issues it is highly recommended to enable a web server to stop information leakage from the server header of an HTTP response.

Web Security Issues 2016: Nginx Version Disclosure
The version disclosure issue is also typical for Nginx and it has the same consequences: the stolen data might help a malefactor gain a greater understanding of your systems, consequently the attacker could plan further attacks with a specific version of Nginx in mind. To prevent your website from this network security issue, add the following line to your nginx.conf file:
|
1 |
server_tokens off |

Web Security Issues 2016: Cross-Site Request Forgery
Cross-Site Request Forgery is another widespread vulnerability. All the functionality available to a website user is also available to a malefactor. Thus, the user is forced to execute such unwanted actions as adding a new user, modifying content, or even deleting data.
Luckily, there is one essential exception: a page that requires extra information such as a password. Therefore, you can prevent the website from this cyber security issue by sending additional information in each HTTP request. The information that only a legitimate user knows can be utilized for determining whether the request came from an authorized source.
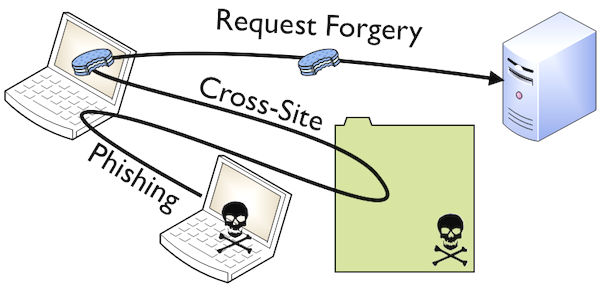
If the attacker does not have access to the user’s account, he will never guess how does your validation token looks like. Hence, a malefactor’s request won’t include a validation token or the token does will not match the expected value, so the server will have a reason to reject this request.
In case of an ajax request form, you can rely on custom HTTP headers can be used to prevent the Cross-Site Request Forgery security issue, because every browser prevents websites from sending custom HTTP headers to another website but allows them to send custom HTTP headers to themselves via XMLHttpRequest (XHR). For a native XHR object, use the following code:
|
1 2 |
xhr = new XMLHttpRequest(); xhr.setRequestHeader('custom-header', 'value'); |
In case of JQuery, a custom header in an individual request requires:
|
1 2 3 4 |
$.ajax({ url: 'foo/bar', headers: { 'x-my-custom-header': 'some value' } }); |
every request requires:
|
1 2 3 |
$.ajaxSetup({ headers: { 'x-my-custom-header': 'some value' } }); |
OR
|
1 2 3 4 |
$.ajaxSetup({ beforeSend: function(xhr) { xhr.setRequestHeader('x-my-custom-header', 'some value'); } }); |
For further information about the CSRF issue, check this articles: and .
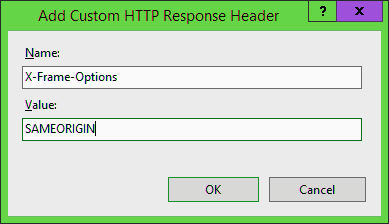
Web Security Issues 2016: Missing X-Frame-Options Header
A missing X-Frame-Options header increases a risk of a clickjacking attack. The appropriate HTTP header field specifies whether the browser should render the transmitted resource within an iframe or a frame. In its turn, a server declares the header’s policy to prevent clickjacking attacks by ensuring that your content is not embedded into other frames or pages.
If you are not familiar with the clickjacking attack, it is based on the following mechanism: an attacker utilizes multiple transparent layers to trick a user and forces him to click on a button or link from another page owned by another app or domain. Thus a user can provide malefactors with passwords, emails, and other credentials via an invisible attacker’s frame while still staying on a friendly website.
The only solution is the usage of proper X-Frame-Options in HTTP response headers. Thus, you will deny framing from other domains in the browser. With the aid of defensive code, you will easily turn your current frame into the most top level window.
X-Frame-Options include three positive values:
- DENY – the page cannot be displayed in a frame.
- SAMEORIGIN – it is only displayed in a frame on the same origin as the page itself.
- ALLOW-FROM uri permits the specified ‘uri’ to frame the page.
More about the Missing X-Frame-Options Header network security issue: and .
Web Security Issues 2016: Forbidden Resources
Probably, access to forbidden resources will be denied by your web server. Note that this is not a sterling security issue, since it doesn’t provide any direct impact on the information security of your website.

Web Security Issues 2016: Email Address Disclosure
You website contains various email addresses. Stolen by malefactors, they can be utilized by spam email engines as well as brute-force tools or be used in social engineering attacks. To prevent the application from this cyber security issue, we recommend you to replace user-specific email addresses with generic email addresses, for instance info@ and contact@, or use submission forms instead.

Web Security Issues 2016: Robots.txt With Potentially Sensitive Content
Another software security issue is related to your robot.txt file. Depending on its content, malefactors might discover some hidden directories of your website by getting access to the file. Therefore, it is extremely important to ensure that your robot.txt does not contain any sensitive data, so don’t write disallowed paths in the file. In addition, you can correctly protect them via authentication.
Web Security Issues 2016: Outdated Software
Outdated software is another common security problem. Since older software is more vulnerable to attacks than its more recent versions, upgrading to the latest stable release is an essential security improvement.
The same is about PHP, so it is highly recommended to upgrade it to the latest stable version. Some known software security issues related to PHP:
- Improper Link Resolution Before File Access
- Denial of Service Vulnerability
- Code Execution Vulnerability
- Code Execution and Denial of Service Vulnerability
- Remote Code Execution Vulnerability
- Denial of Service Vulnerability
- Denial of Service and Code Execution Vulnerability
- Restriction Bypass Vulnerability
- Code Execution Vulnerability
- Denial of Service Vulnerability
- Stack Based Buffer Overflow Vulnerability
- Denial of Service Vulnerability
- Heap Based Buffer Overflow Vulnerability
- Denial of Service Vulnerability
- Restriction Bypass Vulnerability
- Restriction Bypass Vulnerability
- Code Execution Vulnerability
- Sensitive Information Disclosure Vulnerability

If you are using Magento – the most secure ecommerce platform, you should know that the ecosystem contains a lot of problems caused by outdated software.
there are a lot of vulnerabilities related to the platform, your ecommerce business is under a threat. Luckily, you can easily fix all problems by upgrading your ecommerce website to the latest stable version. Alternatively, you can install patches and still use the older Magento version you have always worked with.
For further information about patches, read this article: Magento security patches.
As for Nginx, there are also a number of security problems related to this software, so it is also important to get the latest stable version of Nginx. The most common software security issues are and .
As you can see, the usage of outdated software makes your website much more vulnerable behind a plethora of information security issues.
Web Security Issues 2016: Full Path Disclosure
If your website is affected by the Full Path Disclosure issue, malefactors get the ability to see the path to your webroot/file required for the load_file() query within a SQL injection – a technique used for viewing the page source.
This cyber security issue may produce various outcomes. If your webroot is getting leaked, malefactors may abuse the information and use it in combination with the file inclusion vulnerability. As a result, attackers will get access to configuration files of both web app and the rest of the OS.
For further information, read this article: .
Web Security Issues 2016: Unexpected Redirect Response Body
An unexpected redirect response body (it is often too large) indicates that the page do not finish the response as it was supposed to after a redirect. This problem leads to such network security issues as the authentication bypass in authentication required pages, while in other pages it indicates a programming error.
To prevent your website from the problem, you should:
- Finish every HTTP response after redirecting a user.
- Replace Response.Redirect (“redirected-page.aspx”, false) with Response.Redirect(“redirected-page.aspx”, true) in ASP.NET.
- Call exit() after redirecting a user in PHP apps.
Conclusion
Although, there are lots of other web security issues, the aforementioned ones are the most common. By fixing them, you will significantly improve a current level of safety represented on your website.
If you are a Magento merchant, don’t forget to check our Magento Security Guide.
And don’t hesitate to ask us via the comment field below, since we are here to help you. Besides, you can inform us and other Firebear’s readers about web security issues missed in this post.