Magento First Aid: Threat-Detection, Monitoring, Medication, Analepsy, & Immune Stimulation For E-Commerce Websites

In the following article, we share all the information necessary to bail up a hacked Magento website (no matter, it is Magento 1 or Magento 2) and prevent possible inbreaks. Commonly, the most significant concern is that you may not even know that your e-commerce store has been attacked. Therefore, it is necessary to check whether such an episode took place or not. If offenders got claws into your business, you have to clean up an infected Magento site and extinguish the malicious impact. Moreover, it is necessary to take care of further possible intrusions. To help you with that, we discuss how to identify, fix, and protect your Magento installation and encapsulate information about the most prevalent break-in types and ways malefactors turn e-commerce stores to their advantage.
Table of contents
Common Issues
So, what signs show that your Magento website has been stricken?
Firstly, you may start receiving blacklist warnings by search engines, such as Google or Bing. Strange credit card activities reported by your customers indicate that something is wrong. An abnormal checkout page behavior may be considered a lucid trace of offenders. The appearance of spam keywords in product listings or SERPs doesn’t semaphore anything good. So are various wicked activities that often lead to the suspension of a website. File modifications, Magento core integrity issues, unknown admin users are also among the most spread symptoms of a contaminated Magento website.
Whenever a store is corrupted, the stolen customer credit card data is among the top concerns. The problem is especially harmful if you rely on Magento to process payments. In this situation, it is necessary to respond to a possible data breach on your own.
However, most businesses choose to deal with payments off-site. They rely on secure payment gateways, API integrations, or third-party payment forms. Such tricks secure customer data against digital theft.
Since the list of possible inbreak scenarios is almost virtually endless, let’s return to it later. Now, we’d like to proceed with effective threat identification strategies.
How to Check Whether Your Magento Website Has Been Hacked
Below, we share several first aid measures designed to help you detect diseases and heal the wounds of your Magento website. So, what is the number one advice?
Scan Your Store
The more insecure the Internet becomes, the more protection tools are available for free. And e-commerce, despite it involves a significant amount of money, is not an exception. Various online tools enable you to scan your Magento installation at no cost, without third-party specialists, remotely. It means that identifying credit card scammers, malicious payloads, unsecure domains, and other thorny problems is no longer an unsolvable issue.
You can scan your Magento website for malware and other insecurity points with the help of , , or similar software solutions. The procedure is as intuitive as possible: visit the checker, enter your store URL, and initiate the scan. That’s it!

If your website is infected, the system displays a warning message. Pay attention to all reported payloads, locations, and blacklist warnings. Besides, specialists recommend scanning all other websites that share the same server with yours due to the possibility of cross-site contamination. The latter often causes reinfection.
However, a remote scan is not a silver bullet. The process takes place on your website but gains no access to the server. What does it mean?
Well, if a store scan detects no breaches, it doesn’t mean that your e-commerce business is not stricken. While some problems can be detected in a browser (you can monitor your website for backdoors, phishing, server-based scripts, etc.), many challenges are exclusively related to the server. Consequently, the most comprehensive cure merges both remote and server-side scanning.
Server-side monitoring usually incorporates third-party software that verifies files for backdoors, phishing, and other safety gaps that remote scanners don’t see. Some solutions can track file changes, providing a more comprehensive audit.
For instance, Sucuri offers an , which is a free addition to the platform’s regular clean up and monitoring plans, developed to check website files, looking for issues that the remote scanner cannot distinguish.
It also traces alterations, giving you an audit trail of your website file changes.
Follow the links below to scan your Magento 2 website:
- – a free website check and malware monitoring;
- – a platform that delivers a quick insight into the security status of your Magento website and provides advice on how to fix possible vulnerabilities out of charge;
- – an official free store scanner;
- – a solution to look for hidden illicit content built into your web pages;
- – a scanner that provides threat alerts and educational information related to your website soundness via email;
- – an open-source project that is no longer maintained;
- – a tool to look for issues on your website;
- – a remote analyzer of suspicious files and URLs that detects various types of scam and shares them with the community.
Make Sure Core Files Are Integral & Unchanged (Scan Your Server)
Let’s say a few more words about scan techniques that involve server monitoring. Any new or recently modified files on your server may signalize that you’ve been hacked. Therefore, focus on your Magento file system from time to time, detecting malicious injections.
Since all Magento versions are available on , it is possible to download the necessary software locally via an SSH terminal and compare it with the one from your server. Use the following commands in the current order to achieve this goal:
|
1 2 3 4 5 |
$ mkdir magento-2.3.0 $ cd magento-2.3.0 $ wget https://github.com/magento/magento2/archive/2.3.0.tar.gz $ tar -zxvf 2.3.0.tar.gz $ diff -r 2.3.0 ./public_html |
The example above incorporates the Magento version 2.3.0 as a source of clean files. Use a version that suits your particular installation. Besides, you should replace “public_html” with a path to your Magento installation on a server.
The diff command compares files of the clean Magento version with your installation. Note that the output detects not only possible malware but also shows additional modules that you’ve installed.
You can manually check recently modified files following these steps:
- Log into your Magento web server.
- Use this command to obtain all files modified within the last ten days:
1$ find ./ -type f -mtime -10
Replace 10 with any period you want to embrace. - Analyze unfamiliar modifications to detect suspicious files and integrity issues.
It is always a good idea to use SFTP, SSH, and FTPS to access your server rather than FTP. The latter is unencrypted, resulting in additional security breaches.
Pay attention to the fact that some malware infections can be detected due to a changed file modification date. But you can simplify your stalker chores by using one of the following file integrity monitoring solutions:
- – a platform for detecting dangers, identifying vulnerabilities, and checking file integrity for Magento;
- – a tool for monitoring and reporting changes to the integrity of the Magento system and configuration files;
- – an open-source intrusion detection system with FIM (file integrity monitoring) capabilities;
- – a centralized log management solution that detects unauthorized modifications;
- – a cloud application that logs file changes centrally;
- – a sophisticated tool with FIM functionality.
Trace Admin Logs
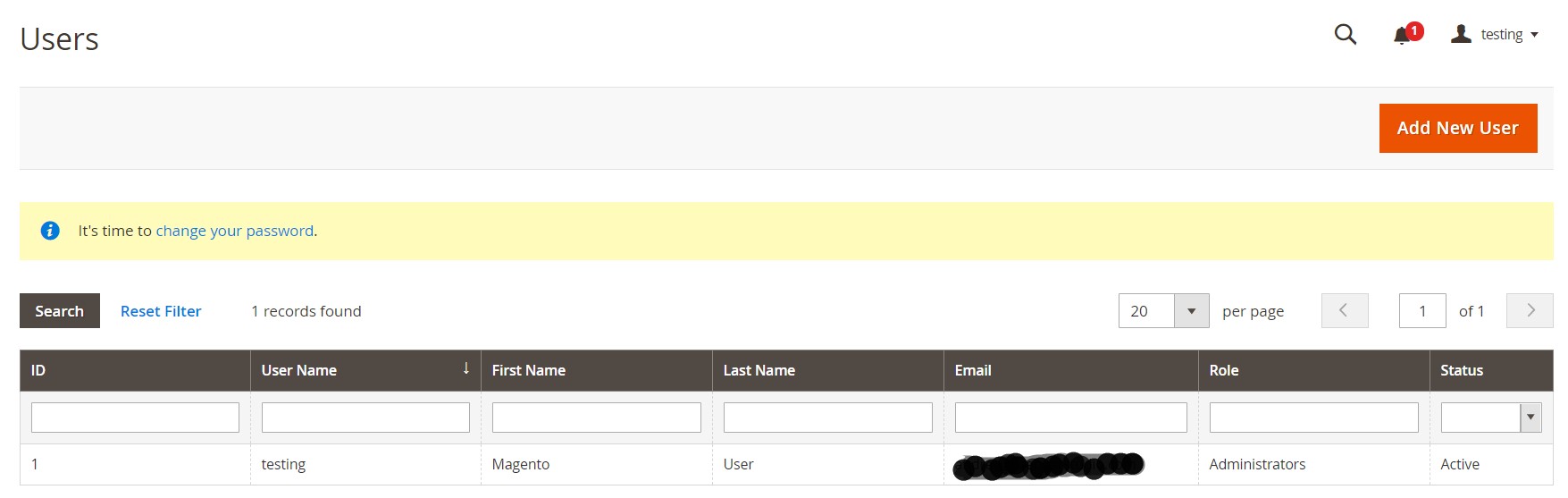
New and unknown user accounts may be considered a red flag as well. Hackers often register new administrators on compromised e-commerce websites to get additional access to store data and gain control over storefronts. Neither Magento 2 nor Magento 1 are immune to this disease. Therefore, verify all admin accounts. You can detect malicious users in Magento as follows:
- Log into the backend of your Magento store.
- Go to System -> Permissions -> All Users.
- You will see the grid with all users there. Review the list for administrators with abnormal or recent ID numbers.
- After further investigation, delete questionable users.
You can apply the same safety measures to registered customers if their accounts seem suspicious (Customers -> All Customers).
As for admin monitoring, there is a more reliable way to trace malefactors. Both Magento 1 and Magento 2 are associated with a wide variety of third-party extensions. And fully-flagged admin loggers take pride of place in the ecosystem. We compare the best solutions here: Magento 2 Admin Logger Extensions Comparison. These tools not only let you detect newly created accounts but also provide the ability to record every step administrators take within the backend. Consequently, you can effortlessly find out what users are compromised.
Behold The Reports
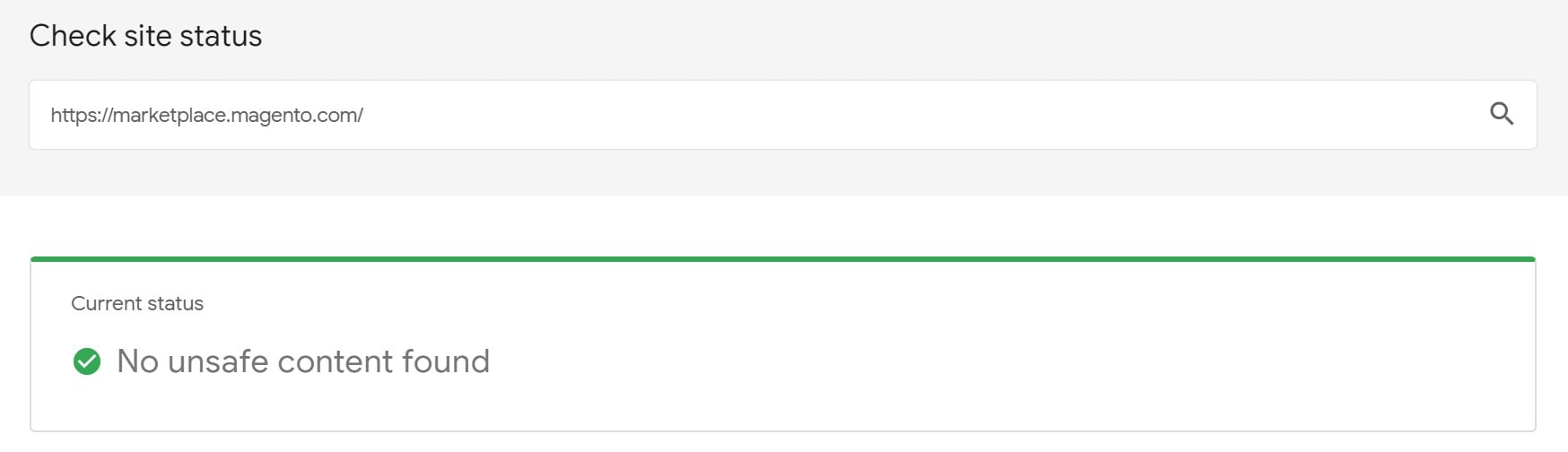
Leverage Google to revise your Magento website for hacks. It is evident that if the search engine blacklists your store, it is time to act. You can consider reports by other authorities if necessary. As for the boss of inquiries, its diagnostic tools represent a reliable way to check the security status of your Magento installation. For instance, there is always an opportunity to streamline your Google Transparency Report:
- Visit the webpage.
- Copy and paste your site URL into the corresponding field.
- Click the search icon.
- Get the status and additional information about the reliability of your website.
Pay attention to the fact that almost all search engines offer free webmaster tools. You can utilize them for regular monitoring. Usually, such services provide ratings and reports for your Magento store. You can find the most substantial solutions here:
- ;
- ;
- .
Your customers are another source of information regarding your security. Always keep in touch with them to discover such issues as fraudulent purchases shortly after ordering. It will help you avert a disaster in the early stages.
Pay Heed To E-Commerce News
The global e-commerce community dynamically reflects all vital changes that impact the entire ecosystem. As a result, information regarding the newest vulnerabilities is always under your disposal. When it comes to Magento, you can always find the latest information about ill-disposed actions in the . If your store hasn’t been compromised, it doesn’t mean that it is a safe place. Therefore, always check the official Magento website for possible vulnerabilities and patches to fix them.
How to Fix Your Magento Website After A Hack
Regardless of whether your Magento website has experienced an attack or just contains a defenseless spot, you need to address the issue immediately. Below, we shed light on how to get rid of Magento security breaches, remove vulnerabilities, and restore justice.
Remove Compromised Files
You’ve just revealed a malicious domain or payload. However, it is not a cause for alarm. Firstly, malefactors may not be able to start their dubious dealings by the time you’ve spotted them. Secondly, it is relatively easy to recover from their misdoing:
- Look for contaminated files on your Magento server.
- Compare infected elements with known right files (as we’ve just described above).
- Identify and remove vicious changes.
That’s it! Make sure the version of your clean reference follows the edition of your Magento core files, including patches and extensions.
If you don’t know how to cure a malware infection, ask a specialist. If you want to do everything without hiring a third-party expert, here is a brief overview of the process:
- You have to be logged into your server.
- Create a backup to be able to restore your Magento website in its current state if something goes wrong after deleting corrupted files.
- Identify recent changes and confirm whether they are legitimate or not.
- Replace suspicious files with their clean versions.
- Review your custom files and remove any suspicious or unfamiliar code from them.
- Verify your Magento 2 storefront: your goal is to remove the contamination and keep it operational after the new changes are applied.
Besides, you can visit community forums, such as , to find help. Chances are, your problem is not unique. Therefore, you may easily find the corresponding topic. If nobody discusses your particular issue, feel free to ask other community members for help.
Note that some specialists recommend taking it a step further by reinstalling all the extensions even when you detect no evil-minded elements in them. Although the procedure is time-consuming, you will ensure all modules are functional and free of malware.
However, several considerable drawbacks are associated with doing everything by yourself. You may overwrite or delete vital files, breaking your store. Eventually, the desire to reduce expenditures will bump costs. If the possibility to bust your Magento website doesn’t frighten you, check these tools for comparing files:
- – analyse text files, documents, binary files, and archives;
- – examine text differences between two text files;
- – check the contrasts of two files in two directories.
Keep Database Tables Clean
Below, we share two approaches to keeping database tables clean. Let’s explore the most user-friendly and safe one first. You can remove a malware infection from your Magento database right under the Content section of your admin. It is possible to edit static blocks, CMS pages, and other dirty content elements of your store there. However, this approach is far from being the most efficient.
Alternatively, it is possible to apply changes at a low-level database admin panel. You can leverage or such tools as or . However, removing code and files manually without any previous experience can be extremely dangerous – the impact of wrong changes may outweigh the destructive consequences of a hack. Therefore, you should always create a backup prior to performing any actions. Or seek professional assistance instead.
If you still think that removing a malware disease from Magento database tables is your option, follow these steps:
- After logging into the admin panel of your database, create a backup of the database.
- Scan and analyze the database to discover suspicious content. It may be links, keywords, or anything else you didn’t place there.
- When a table with suspicious content is discovered, manually remove its wicked elements.
Also, take notice of the necessity to verify that your Magento storefront keeps working after the objectionable content is removed.
Besides, it is possible to dig up malicious PHP functions in your Magento database manually. You can search for such common examples of saboteurs as eval, gzinflate, base64_decode, str_replace, preg_replace, etc. Bear in mind that some Magento malware is located in the core_config_data table in the footer and header area.
Farewell To Hidden Backdoors
Every decent hacker leaves a way to get back into your website after you address the original issue. Therefore, Magento is always so serious regarding the potential bottlenecks. As a Magento user, you’ve probably got tons of emails informing you about newly discovered breaches and patches developed to fix them. You might have noticed that most of such problems usually have zero reports pointing to real break-ins. Even if a potential vulnerability has never been exploited, it doesn’t mean that nobody will leverage it in their vile intent. Therefore, it is necessary to remove all hidden backdoors no matter whether they were created during the previous hacks or delivered as a built-in stain. Let’s explore both cases.
Offenders often mask backdoors via new elements that look like official Magento core files. They usually focus on such Magento locations as the footer or header. You can review them under the Content section of your admin, discovering malware. However, some third-party extensions may modify such locations as well. So, if you remove a benign function, you will probably break the entire website. Ask specialists with the corresponding experience to do that to get out of the rain.
If you want to remove backdoors by yourself, compare the existing Magento files with a clean reference:
- Log into your server.
- Backup the existing site files.
- Compare your store with the touchstone to discover any new files that look suspicious.
- Replace them with known good copies.
- Flush Magento cache and test the changes.
Take into consideration that trespassers often use encoding to prevent detection. However, this practice is quite rare when it comes to the official Magento repository, except its premium components.
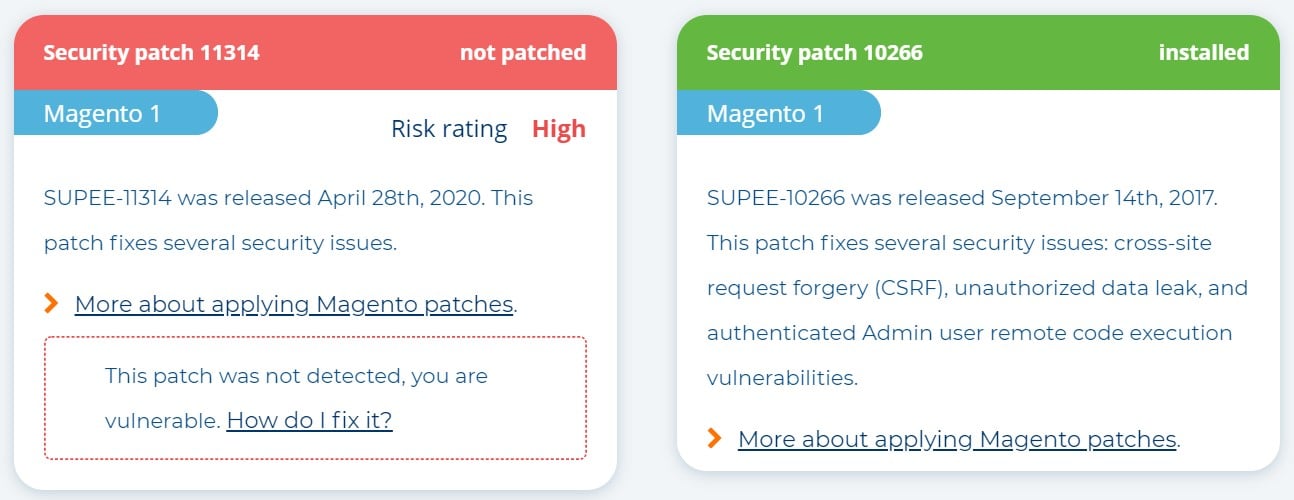
As for the second case, we can only recommend you to apply Magento 2 security patches and regularly update the software. If you still use Magento 1, check our Magento 1 End Of Life Ultimate Guide or . Unfortunately, there are no official Magento 1 patches to close its potential backdoors and address other possible issues. You have to rely on third-party solutions that cannot guarantee 100% safety. As for Magento 2, you can streamline official updates, keeping your installation clean and secure.
Reset Admin Passwords & Follow Admin Security Requirements
What’s the most conventional way to block villains from getting access to your data? Right! It is a robust and unique password. However, it cannot provide unsusceptibility to all attacks. But if you’ve been hacked, it is necessary to reset all admin user passwords to avoid reinfection.
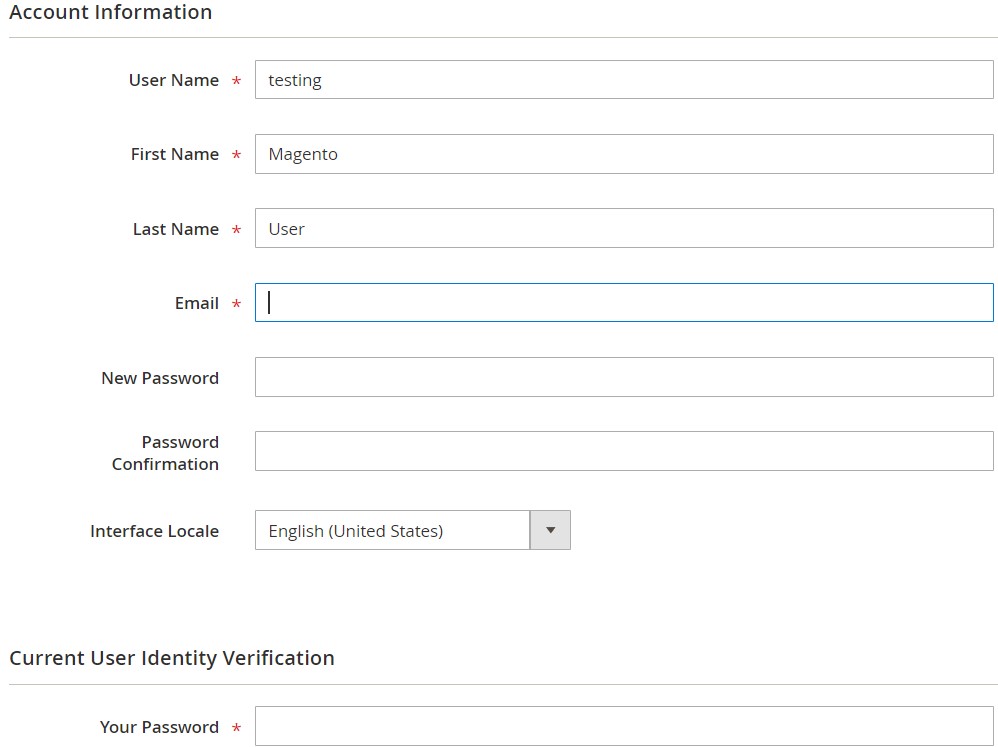
You can remove admin passwords in Magento 2 as follows:
- Select an administrator to reset a password under System -> Permissions -> All Users in your Magento 2 admin.
- In the Account Information section, enter a new password (New Password) and confirm it (Password Confirmation).
- Next, enter your password in the Your Password field to verify your identity and apply the new changes.
- That’s it! Now, you can save the user and proceed to another account.
Specialists recommend reducing the number of admin accounts. Of course, you cannot fire backend managers just for the sake of following this advice. However, many merchants tend to keep unused admin accounts, along with FTP and website system accounts. Don’t do that because you raise the possibility of intervention. At least, villains get additional ways to reach your precious data and gain complete control over your website.
Provide users with access to your Magento admin for as long as it is necessary. After that, you should delete their accounts. Although creating a new user role may seem an unpleasant chore, it is a way less distasteful activity than addressing the implications of an attack.
How to create a reliable password, you will ask? There are three conditions to follow.
Firstly, your password should be complex. It means that it should contain letters, numbers, and symbols.
Secondly, every password should be long enough. Although the minimum required number of characters in Magento 2 is seven, it doesn’t mean that you should create it that short. The longer your password is, the less hackable it is.
Thirdly, your long and sophisticated password is reliable only if it is unique. Don’t use the same combination of letters, numbers, and symbols twice.
What else can make your admin less sensitive to attackers? Magento promotes a multifaceted approach that combines several techniques available out of the box.
First of all, you can hide your backend section from offenders. It is only necessary to use a custom Admin URL that is hard to guess. Consider “Admin” or “Backend” obvious and much less secure. Your company name is also not the best possible option.
Two-factor authentication is another trick that dramatically reduces the possibility of breaking in. A token generated on a separate device provides administrators with an exclusive way to verify their identity.
Besides, the admin security configuration enables you to add a secret key to URLs, apply case-sensitive passwords and usernames, as well as use limited admin sessions. You can specify a password lifetime and the number of login attempts to lock an account if it is exceeded. Magento 2 can even monitor keyboard inactivity before the current session expires and require a CAPTCHA. Follow this link to find out how to configure all these and other parameters to turn your admin section into an unassailable fortress: .
Last but not least, your Magento admins should keep their computers clean. Otherwise, your e-commerce website can get reinfected.
Request A Review To Fix Malware Warnings
Being blacklisted by Google or other webspam authorities provides a long-lasting impact on your e-commerce business. However, you can reduce it by requesting a review when the ramifications of the breaking in are fixed. Unfortunately, the process has several nuances you should be aware of: Google may reduce the number of requests that you can send. To make the Internet a safe place, the company sets a limit on repeats for offenders who knowingly host/spread malware through their sites. De facto, every website, which requests a check but is still ill, gets only a single review per 30 days. Therefore, you should know for sure that your Magento website contains no malicious code before requesting a review!
Usually, removing warnings looks as follows:
- Ask a hosting company to remove the suspension.
- Provide details regarding the addressed issue.
- Fill in a review request per blacklisting authority.
- Sit tight: the review process usually takes up to several days.
Post-Hack Safety Strategy
Now, when all vulnerabilities are detected and fixed, you can apply several essential enhancements to reduce the possibility of future attacks to the bare minimum.
Regularly Update Your Magento Website
Perhaps, it is the most obvious advice which is always underestimated. It is not a secret that the number of Magento 1 websites is much higher than the number of Magento 2 storefronts. Even the lack of official support leaves most merchants undaunted. The implications of such dereliction may be dramatic due to the fact that unpatched and outdated software is one of the leading causes of contamination.
Magento 1
The bad news is that you no longer can update your e-commerce website with official protection patches. Although there are a bunch of third-party projects developed to maintain Magento 1 after EOL, we recommend migrating to Magento 2.
The good news is that you can avoid numerous headaches, using our Improved Import & Export extension and its Migration add-on. The two solutions allow moving all entities between the two platforms, so there is no need to recreate them on a new Magento 2 website manually. for further information: we provide migration services, seamlessly transferring Magento 1 storefronts to Magento 2.
Magento 2
Conversely, the situation with Magento 2 is partly the same. The platform’s older versions are no longer supported. Since no migration is necessary, you just have to update your software. Perhaps, the company tries to prevent the sequence of events peculiar to Magento 1, but it is a topic for another discussion. How should Magento 2 merchants act to keep their business safe?
It is necessary to update not only all Magento components, including core files, templates, modules, and plugins but also other outdated software on your server.
Follow these steps to apply Magento patches:
- Create a store backup.
- that suits your Magento version.
- Upload its files to the root directory of your Magento 2 installation.
- Go to System -> Tools -> Compilation and disable the compiler if applicable.
- Use SSH to connect to your website and run the following commands, replacing “your_patch_name_111″ with the name of your patch:
12345sh your_patch_name_111.shpatch --p0 your_patch_name_111.patchunzip -o your_patch_name_111.ziptar -zxf your_patch_name_111.ziptar.bz2 tar -jxf your_patch_name_111.zip - Test your Magento storefront to make sure it works correctly.
- Relaunch the compiler if it was disabled.
- Refresh cache (Flush Magento Cache) under System -> Tools -> Cache Management.
You can apply security updates in a separate development environment first to prevent possible issues. Check the official guide for more detail: .
Enable Backups
Although the Magento backup functionality is deprecated as of 2.1.16, 2.2.7, and 2.3.0, you can still rely on third-party solutions to avoid any information loss. For instance, you can depend on that works both on-premises and in the cloud. The tool provides the ability to back up your database while in production, without affecting uptime. And, of course, you can entirely automate your backup processes.

No matter what third-party backup solution you use, there are several tips to follow.
Firstly, you need to store your backups in an off-site location – not on your server. The reason to do so is safety. If backup files are stored on your server, malefactors can steal them to compromise your Magento 2 storefront.
Secondly, it’s better to make copying frequent and automated. Thus, you will never lose the latest version of your website.
Thirdly, make sure that all the data, including all file formats, are supported by the selected backup tool. Otherwise, you will need to recreate parts of your Magento store manually, after restoring its saved copy.
And don’t forget to test your backups from time to time. Thus, you will confirm that both the selected software and your store work correctly.
Don’t Underestimate Computer Scans
All users who have access to your Magento admin should regularly run a scan with a reputable antivirus program on their computers. Sorry for touching this point once again, but a user with an infected device can compromise Magento, accessing the dashboard. Therefore, it is better to go over the top with safety measures than disregard this tiny advice and let offenders get access to your e-commerce website. Take into account that the world of digital threats is so abundant that it even includes plagues that jump from a computer into a text editor or FTP client, contaminating further instances.
Luckily, the selection of reliable antiviruses is also broad. For instance, you can streamline such commercial options as and or lean on such free software as and .

Another evident notion that we cannot overlook is related to the correct use of malware detection programs. Only a single application should run on your computer, actively safeguarding it from the menace. Otherwise, you will face conflicts occurring between several software solutions, which cause dramatic performance slowdowns.
Use Website Firewall
Hackers consider Magento a coveted prize as it gains new users and accumulates more customer data within all the ecosystem’s storefronts. Therefore, such an additional protection layer as a firewall is a must-have enhancement even if you depend on off-site payment processors that store sensitive customer data far away from your website in a much safer place. By implementing this measure, you eliminate various potential vulnerabilities as well as restrict unauthorized users from accessing your admin area.
What exact perks does a firewall offer?
- Become Insensitive to Known Illnesses. Consider a firewall an immune system that detects and stops all known infections. Of course, it won’t save your Magento website from something utterly new and completely unknown, but the Internet is teeming with identified threats of all forms and measures. So, it is better to get shielded from them.
- Get The Latest Security Inoculations. Every bleeding-edge illness becomes explored and transposed to known issues right after the first few reported cases. Specialists successfully create vaccines, making a firewall immune to recently unfamiliar diseases. Since the protection exists independently from your e-commerce store, it is automatically inoculated, providing up-to-date assurance mechanisms even if you forget to apply the latest patch to your Magento website.
- Keep Bullies Behind The Fence. A website firewall eliminates attempts to use brute force automation to get your passwords. Besides, it detects and blocks all types of DDoS attacks. As a result, malefactors cannot get your sensitive data or break your Magento 2 storefront.
- Get Fit. Most firewalls not only save your website but offer various performance optimizations too. For instance, you can use advanced caching to increase the existing page speed.
Stay PCI Compliant
We won’t squander time describing how substantial PCI Compliance is – its significance is hard to overestimate. However, Magento 1 has recently become a Gordian knot in terms of the requirements created by major credit card companies. Designed to stop credit card theft, these conditions can no longer be followed since Magento 1 doesn’t get official updates. (Check our Magento 1 End Of Life Ultimate Guide for further information and regarding the migration to Magento 2.)

Unfortunately, PCI incompliance not only degenerates the security of your website but also prevents credit card processing systems from working with you. The implications are devastating. But you can avoid them following these technical and operational measures:
- Firewalls. Keep your Magento website under a firewall.
- Passwords. Do not use vendor-supplied passwords. Use strong, long, and unique combinations of characters.
- Cardholder Data. Shield cardholder data stored on your Magento website. Restrict access to it.
- Data Encryption. Encrypt cardholder data transmission across public networks.
- Antiviruses. As we’ve mentioned above, it’s a good idea to defend all systems against malware as well as keep the corresponding software updated.
- Software. Use the latest versions of Magento 2, third-party extensions, and other solutions you use.
- Data Access. Require unique IDs to access data, maintain access logs, and implement physical access restrictions.
- Vulnerability Monitoring. Track all approach lanes to network resources and cardholder information, test security systems, and processes.
You can find more information on PCI compliance here: .
Official Magento Security Practices
Magento offers a wide-ranging list of protection practices and defense mechanisms. Since we are talking about a successful post-hack safety strategy, it is necessary to highlight the fundamental concepts of this guidance. A multifaceted viewpoint on improving the reliability of your Magento installation describes enhancements that you can follow to make your site less vulnerable.
Before working on a new Magento project, you should consider these two aspects:
- Credible Partners. You can prevent numerous possible issues by choosing a reliable hosting provider and solution integrator. Evaluate their qualifications, read reviews, ask other clients, and, of course, discuss their approach to safeguard. A trustworthy partner should always have a secure software development life cycle in concert with such industry standards as .
- HTTPs. Launch the entire site over HTTPs. In addition to security, it is a strong ranking factor. If you already have a Magento website, create redirects from HTTP to HTTPs.
Safe Surroundings
Next, it is worth thinking about the protected environment for your e-commerce website. This part of the guide is especially essential since your installation is only as secure as its weakest point.
First of all, it is necessary to prepare the server environment. Make sure its operating system is secure, and no unnecessary software is installed on the server. Disable FTP since it is totally unsafe. Use SSH/SFTP/HTTPS due to the top safety level they provide. Keep all system files and directories adequately preserved. Magento recommends not only using strong and unique passwords but also changing them from time to time. System updates, patches, and monitoring are among the best practices as well. Last but not least, the guide puts an emphasis on user access restrictions.
Besides, there are several advanced security recommendations to follow:
- Enable automated deployment;
- Utilize private keys for data transmissions;
- Install third-party extensions outside your production server;
- Use whitelists with the IP address to restrict admin access;
- Enable admin logins via two-factor authentication;
- Remove “development leftovers” and unnecessary unprotected files from your server;
- Use only requires outgoing connections;
- Utilize a Web Application Firewall.
You should watch out for server applications. Make sure that all of them are secure and updated. According to the guide, it is better to avoid running other software on the same server with your Magento installation. For instance, offenders can exploit potential WordPress blog vulnerabilities to expose private data from Magento.
The admin desktop environment is another area to control and uphold. All devices used for accessing the Magento backend should be secure. You can follow this requirement by updating your antivirus software as well as using a malware scanner. Besides, avoid unknown programs and suspicious links, use strong passwords and password managers, and never save FTP credentials in FTP programs.
Protected Magento
As we’ve just mentioned, the credibility of your e-commerce website starts with its initial setup and covers a broad spectrum of enhancements:
- Use the most recent Magento version with the latest security enhancements. Install all patches if you cannot run a full-fledged update.
- Create a unique, custom URL for your Admin area.
- Carefully review and configure endpoints that can initiate safety issues.
- Restrict external access to development, staging, and testing systems.
- Use file permissions correctly. Some files should be set to read-only.
- Your Magento Admin should be hidden behind strong and unique passwords, two-factor authentication, CAPTCHA, etc.
- Choose only trusted extension vendors.
- Avoid suspicious links, emails, and files.
- Develop a disaster recovery plan (like the one described in this article).
- Enable automated backups for your server and database to an external location.
You can find the complete guide here: . Also, check this PDF documentation: .
Prevalent Hacking Methods
This guide won’t gain its full value without the most spread malevolent techniques being described. The information below will help you reinforce the understanding of the safety problems to struggle with malefactors way more efficiently.
- Viruses & Malicious Code. Hackers can exploit various website’s vulnerabilities to install their malware. There are illnesses galore for every possible bottleneck, website section, malevolent intent, etc.
- Brute Force Attacks. This technique is quite straightforward. Offenders try various password combinations until finding one that fits a website they are trying to kick in. However, there is a simple solution – you just need to limit the number of unsuccessful login attempts.
- DoS\DDoS. The goal of any Distributed Denial of Service attack is to make a certain server unavailable by using bots, sending an enormous amount of requests that cannot be handled. Such tremendous attention to a website results in a crash that usually happens in a relatively small amount of time, but requires much more resources to be fixed.
- Phishing. This cybercrime looks as follows: a transgressor contacts a target by email, telephone, or text message, posing as a legitimate institution. Next, the trespasser lures the individual into providing sensitive data such as personal credentials, banking and credit card data, and so on. From the e-commerce perspective, this method implies the replication of a website or its parts with the same aim. Once a customer enters their credit card details, a miscreant gains immediate access to that data.
- UI Redress. Although it resembles phishing, UI redress has several distinctive features. While violators also piggyback on an e-commerce website, they leverage it for redirecting users to an unfamiliar spot of the Internet, which usually displays inappropriate content.
- Cookie Theft. Browser data is another item that attracts digital burglars. They can leverage various software to gain access to passwords and other credentials necessary to log into the Magento admin. Luckily, the good old two-factor authentication blocks this onslaught on privacy and security.
- DNS Spoofing. Transgressors streamline old cache data you might have forgotten about along with vulnerabilities in the domain name system to implement DNS cache poisoning. Thus, they redirect traffic from your e-commerce store to a malicious website, programming the attack so that the infected server affects other DNSs, spreading the disease all over the web.
- SQL Injection. Hackers love vulnerabilities in SQL databases and libraries. Such bottlenecks offer the ability to access confidential information by deceiving the system. Simply said, it is a placement of code in SQL statements, using web page input, when the data is either incorrectly filtered or is not strongly typed. Attackers utilize this method to tamper with existing information, spoof identity, cause repudiation issues, or perform complete disclosure of privacy.
- Keylogger Injection. Keylogger is a malware solution for recording computer user keystrokes developed to thieve passwords and other sensitive information. Offenders can streamline it to get access to the credentials of your Magento administrators. That’s why it is so important to have the latest antivirus protection installed on the computers of your employees.
Heed that most strikes are non-targeted. They are like a natural disaster. Malefactors quickly discover websites with similar weaknesses, using Google’s Hacking Database or other sources. For instance, stores that have a vulnerable plugin installed often become a target of miscreants. However, there are always exceptions, and some of them affect Magento, which often suffers from Magecart attacks.
Magecart Threat
The final chapter of this article describes Magecart and the dangers it poses. The consortium of hacker groups usually targets online shopping cart systems, especially Magento, with a single aim – to steal customer payment card information. Offenders compromise a piece of third-party software or infect unprotected industrial processes.
First Magecart attacks date back to 2014 when the group of prowlers monetized stolen credit card details for the first time. Since then, the number of Magecart’s victims has risen dramatically up to . Although Magento is not the only target of the group, it experiences its most significant impact due to the popularity of the platform among the most prominent market players. However, small stores are also in the limelight.
Specialists divide the Magecart environment into 6-7 different groups that obtain unique infrastructure, have specific targets, and wield special techniques, but bear the same common goal of fetching credit card details and selling them on the black market.
- Groups 1 & 2 target a wide variety of e-commerce stores. Members of both groupings rely upon automated tools to breach and skim Magento websites.
- Group 3’s routine involves digging up vulnerable websites and hitting them in bulk. Such assaults may reach an unexpectedly colossal scale.
- Group 4 is exceptionally advanced in applying various sophisticated hack techniques. A transgressor blends in with a targeted website, avoiding detection for as long as possible.
- Group 5’s inbreaks usually lean on third-party solutions. Pieces of code are installed into a vendor’s product, which targeted websites incorporate.
- Group 6 is most selective in its targets, among other Magecart fractions. Its members target top-tier companies only, using various tools and methods. The grouping’s most prominent victims include British Airways and Newegg.
Despite some principal distinctions between the groups, most Magecart assaults on Magento share the following key steps:
First of all, offenders gain access to a Magento website. Depending on a group and other conditions, this process usually differs a lot. However, the goal varies to no extent – hackers exploit vulnerabilities to invade the backend realm of a website.
Next, Magecart members modify the store’s source code. They primarily inject ill-disposed JavaScript to control the checkout page along with its payment forms, obtaining data customers provide to complete a purchase.
Then, the skimmed data appears on the black market. It is sold and used to make unauthenticated online transactions.
Upshot
Let’s encapsulate the most common sources of threats you may face as a Magento merchant and recall tactics to stave them off.
- Vulnerable scripts and viruses allow burglars to crawl into the control panel of your Magento store. Apply the latest patches and update your software to decrease the possibility of accessing your website’s files, database, or admin panel to a bare minimum. The faster you do that, the more chances you have to keep your online business uncompromised. Thieves rapidly master and exploit new weaknesses, so you have no time to wait.
- Susceptible plugins and templates represent another source of headaches. By using free solutions or downloading commercial extensions and themes on torrent websites, you risk seriously. In the first case, the software is usually uninfected but may contain lots of vulnerabilities that hackers will potentially exploit. In the second case, you may get tools that already include malicious scripts. Purchase templates and modules only on official marketplaces or right from trustworthy vendors.
- Insecure communications are as dangerous as hell. If you connect via FTP, malefactors can easily steal your login and password. Use only secure connections to avoid unpleasant situations.
- Server or hosting hacks often put e-commerce websites at significant risks too. No matter if you are a neighbor to a contaminated site, or your server contains other breaches, it is necessary to address the existing issues as fast as possible.
- Regular employees and occasional contractors threaten security by using faint passwords, accessing your admin from infected devices, or even building some code into your website to exploit it later. Therefore, use only strong and unique passwords, protect people who access your Magento admin, and be careful with the specialists you hire.
Running an e-commerce website is associated with numerous risks. However, you can mitigate their impact on your business by addressing the existing safety concerns. Follow the tips this guide kicks around to turn your Magento website into a safe shopping spot where buyers have no reason to worry about, except better purchase decisions to take.

